
Table of Contents
Attack Surface: What is it?
Attack surface is the whole structure of a company, a system or a critical infrastructure that is open to attackers. Systems’ digital fingerprints, digital assets, the technologies being used, versions, secret keys and application paths increase the risk of attack surface. The more digital assets and fingerprints, the higher the threat factor.
What steps do hackers take?
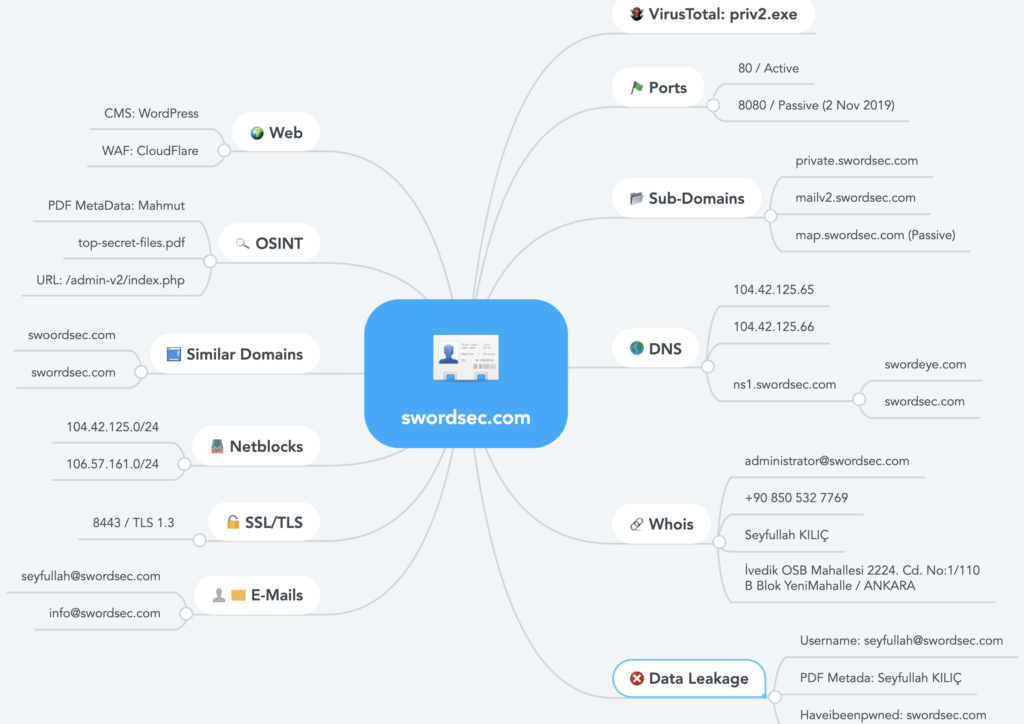
Hackers mostly focus on the attack surface in order to take over systems. Every bit of information they can gather is important for them. The diagram below shows how hackers would take over systems because of a data leak from a web server that hasn’t been updated for a long time.
Simple Scenario 1
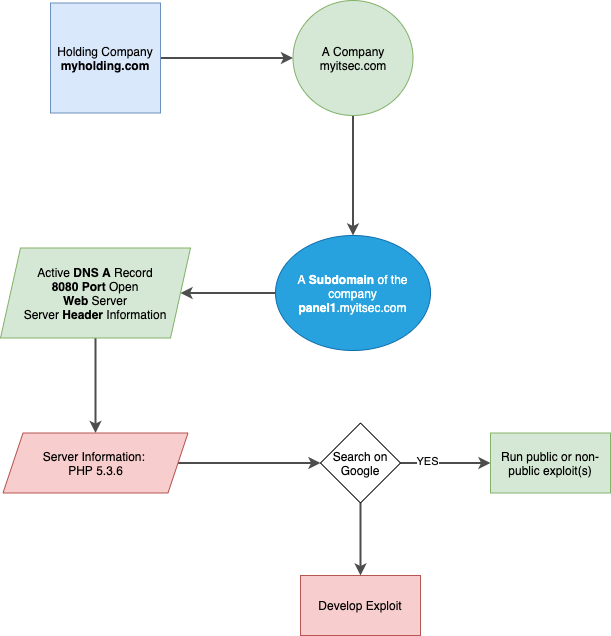
Example below shows dozens of PHP version 5.3.6 that is vulnerable.
Attackers assess all the exposed information and they use endpoints in order to execute sophisticated cyber attacks. Attacks such as encryption, ransomware, and phishing actually occur because of the exposed information on the attack surface.
MITRE Attack has all the data of attacking methodologies and techniques occurring on real world available. (https://attack.mitre.org/matrices/enterprise/)
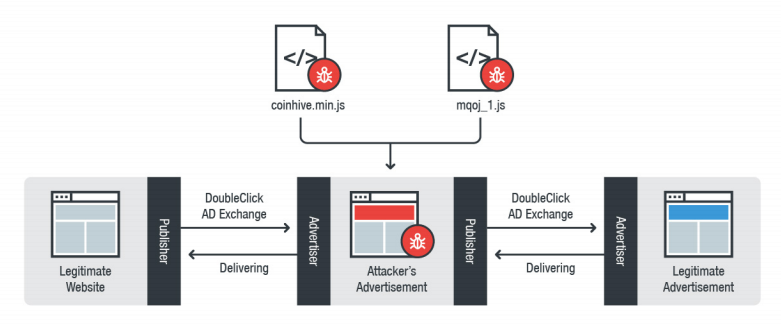
A complex attack with the power of Javascript
Browser based Javascript frameworks that are used for crypto mining highly appeals to hackers. In 2018, attackers gained control of an advertisement company’s systems and even managed to run malicious Javascript code on YouTube. Sources state people’s browsers that played videos whilst the occurring attack mined cryptocurrencies for some time.
Big Data and OSINT
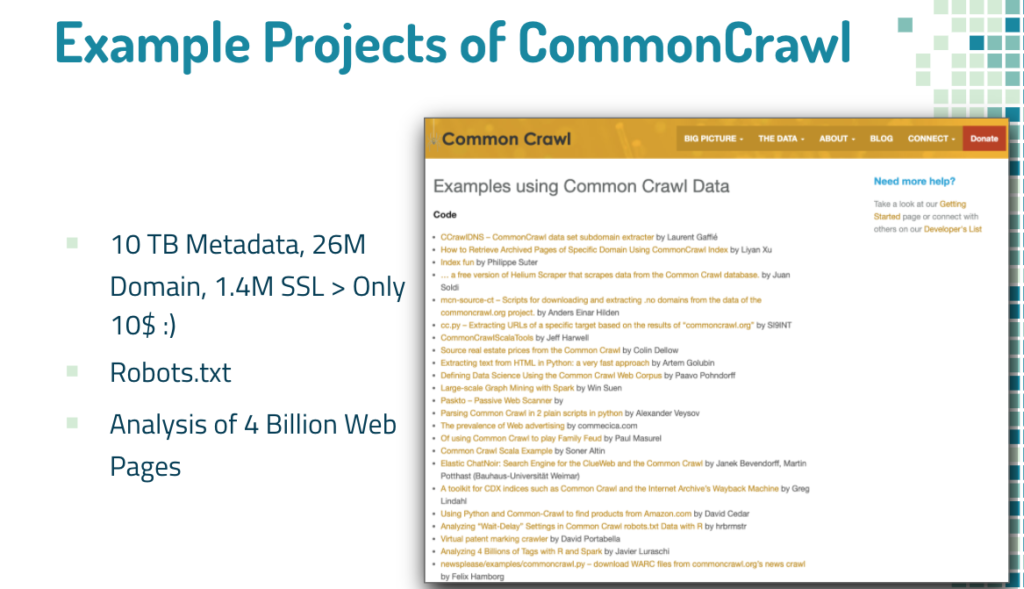
Attackers can obtain petabytes of information about a target from sources such as CommonCrawl.
Parsing 10TB of Metadata, 26M Domain Names and 1.4M SSL Certs for $10 on AWS
In the blog post above, 26 million domain names and 1.4 million SSL & metadata analysis is shown. Attackers can benefit from data exposals from the past, take over random targets or even specific ones and use these exposals for phishing, further exploiting, etc. (Mitre Attack T1598: https://attack.mitre.org/techniques/T1598/)
Internet Devices and Service Search Engines
At first search engines mostly just indexed website contents but then they evolved for images, videos, file extensions, etc.
Today, search engines can list IoT devices, DNS storage data and infrastructures, internet devices and more.
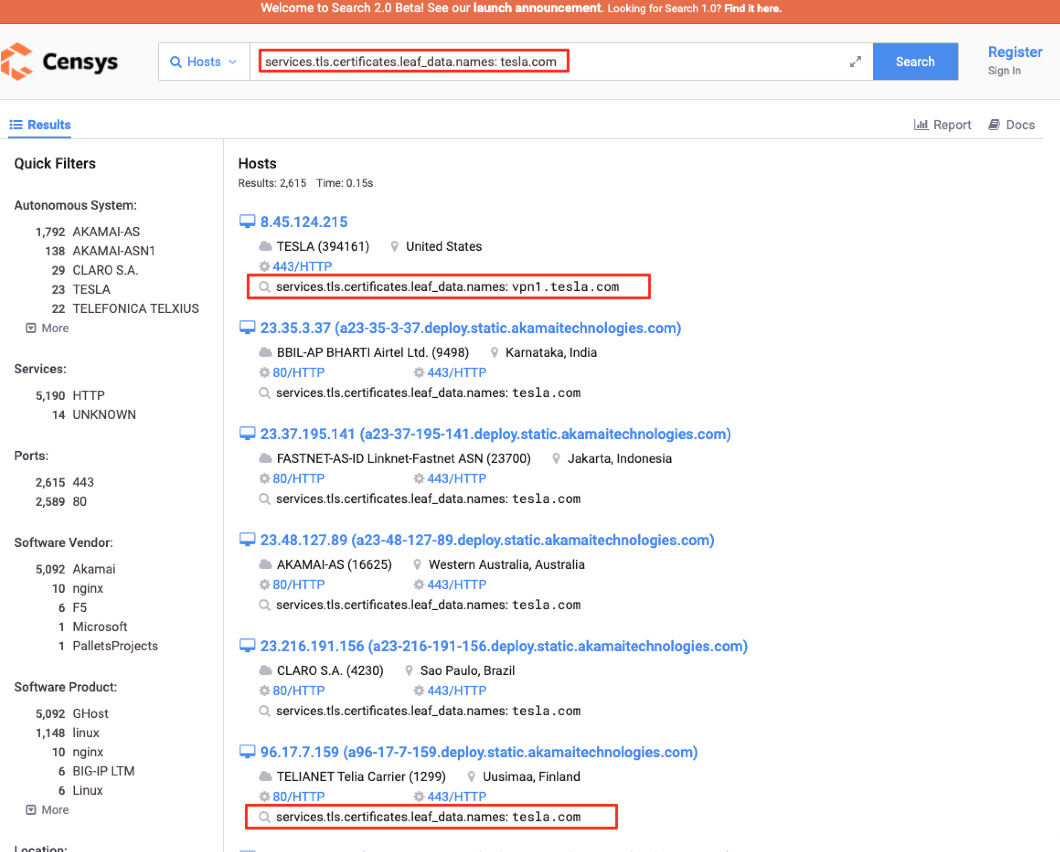
Using pre-crafted queries on these search engines one could easily access IP addresses of hundreds of vulnerable, misconfigured devices and devices that are accessible without any authorization. The key part here is information exposed and states of your organization’s or company’s domain name and the subdomains that are connected. For example information about “tesla.com” domain name is accessible by the said search engines, at least partly. “Partly” because there aren’t a lot of engines that connect DNS data and service data.
Shodan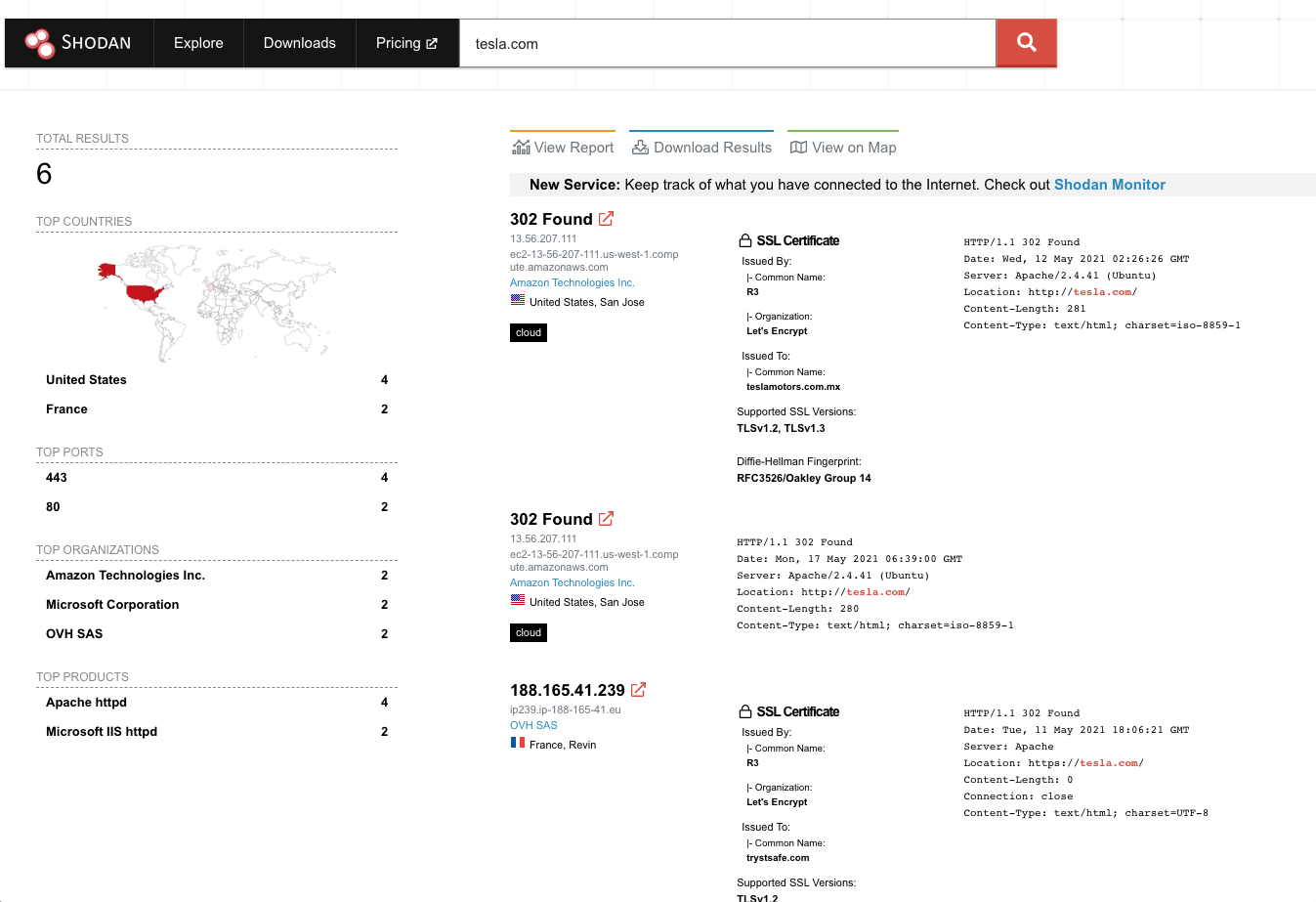
Censys SSL Search
ZoomEye SSL Search
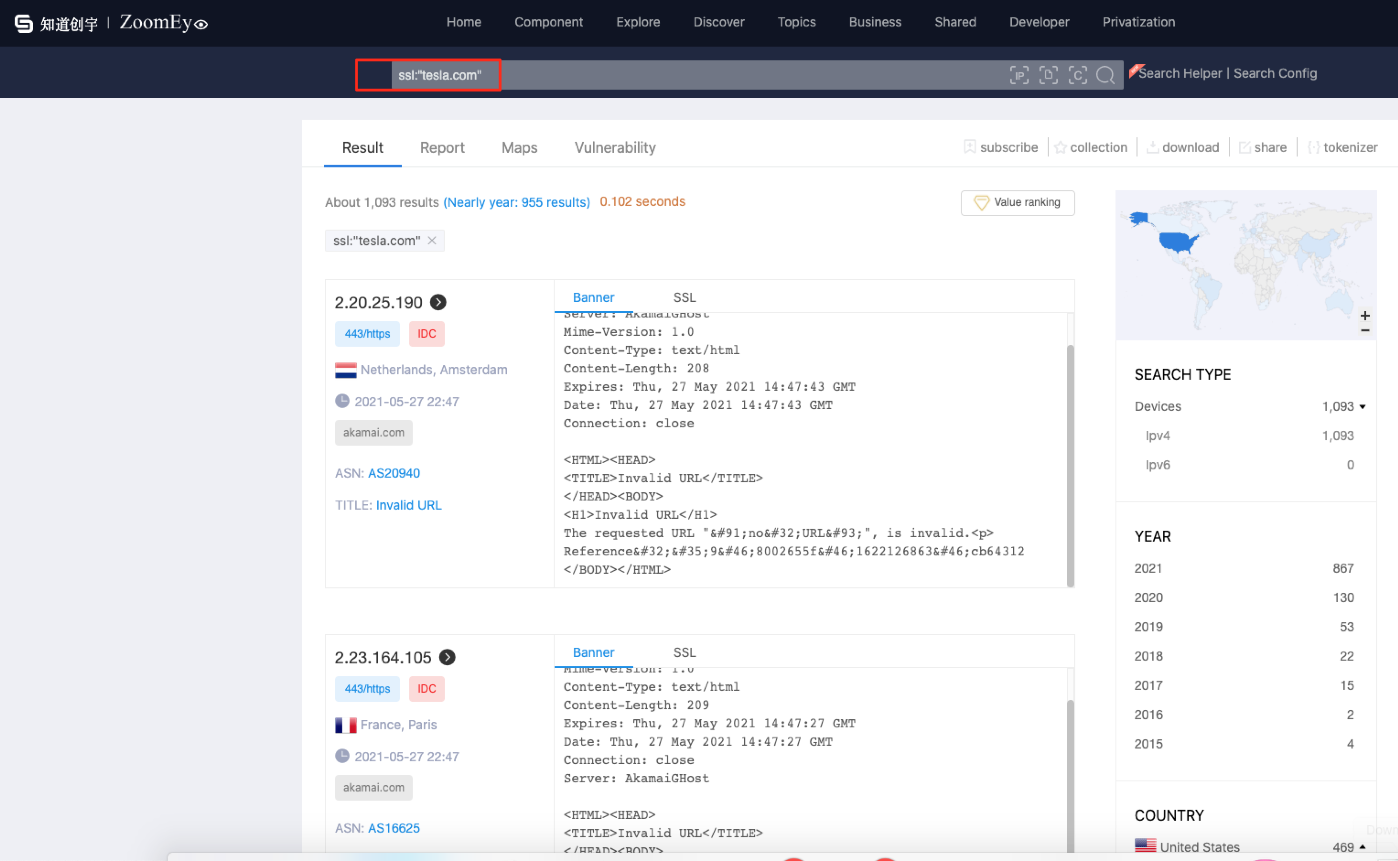
BinaryEdge SSL Search
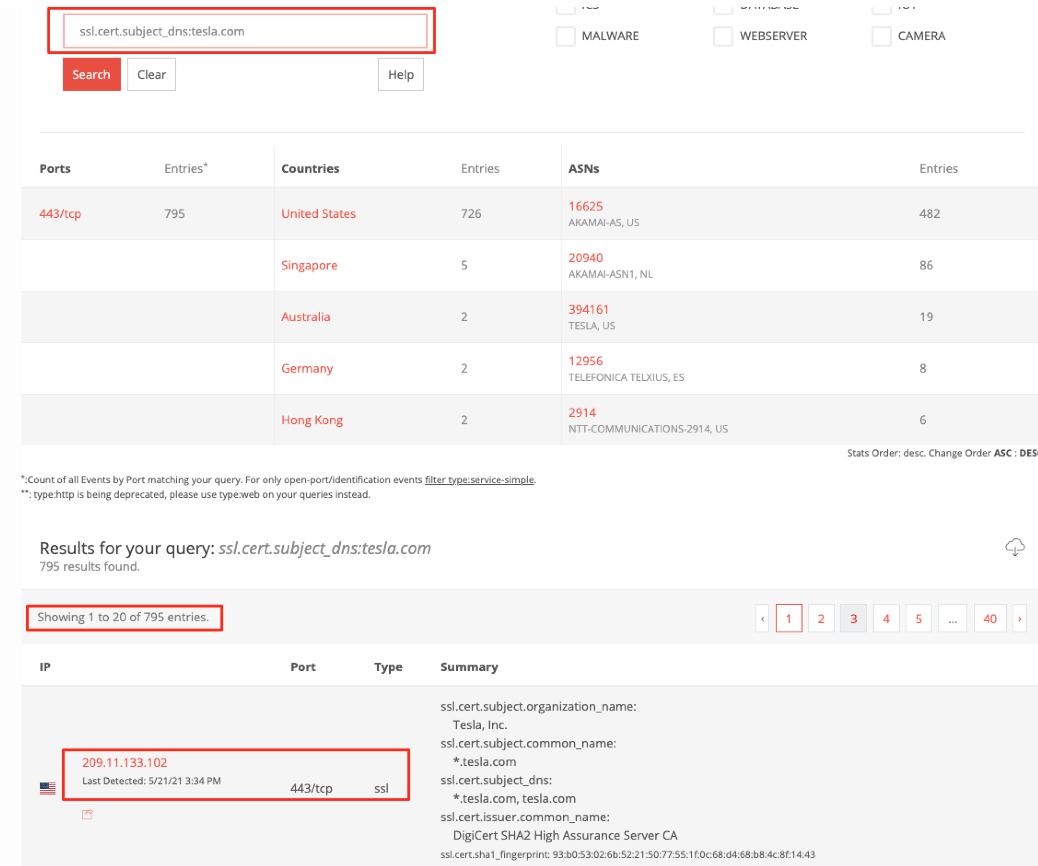
SwordEye
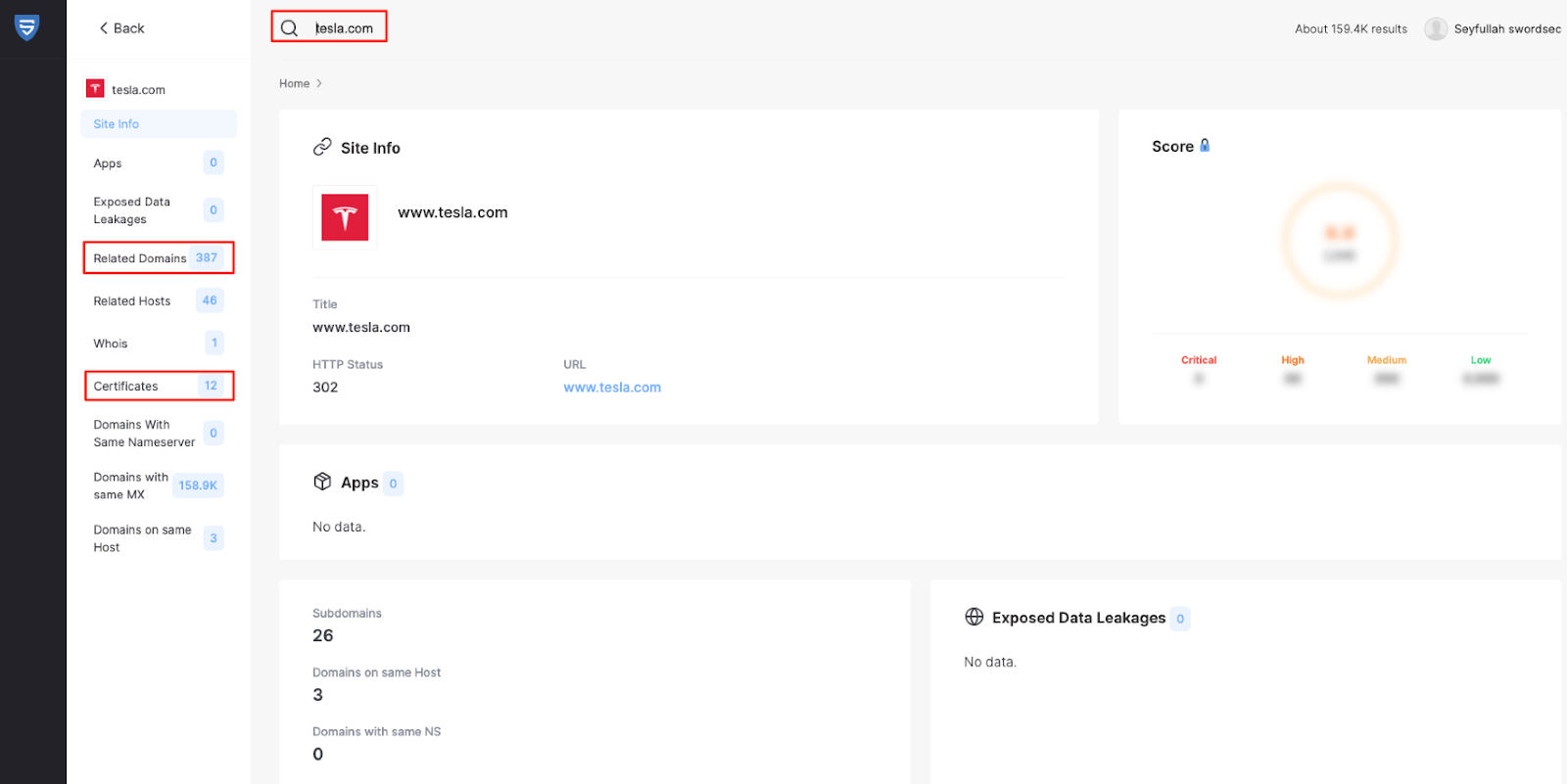
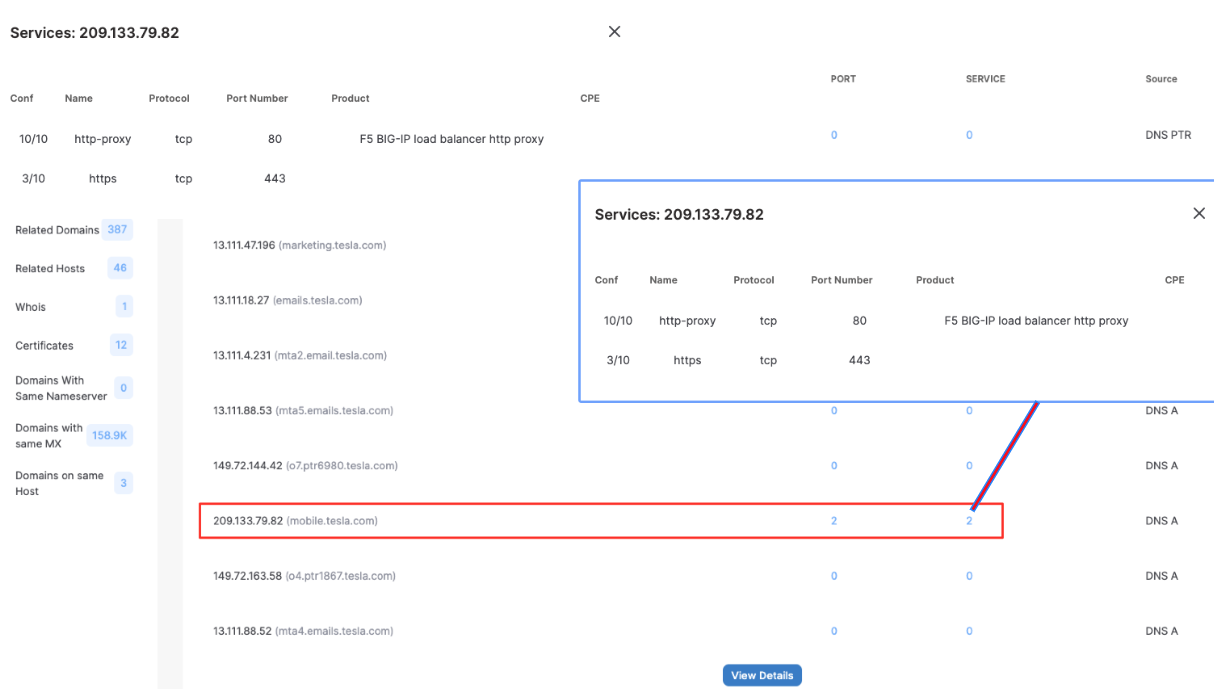
SwordEye’s tesla.com results show that one of Tesla’s subdomains has an open port and a service running on it. Normally searching tesla.com, finding the open port on a domain that has an A record running on the DNS service would’ve taken much longer. SwordEye matches the IP-port and DNS data and shows all of the information related to the domain. Your data that could be found by search engines, your SSL information and your service exposals need to be removed in order to lower your attack surface. You could also take some security precautions so that search engines can not scan your servers, like IP blocking.
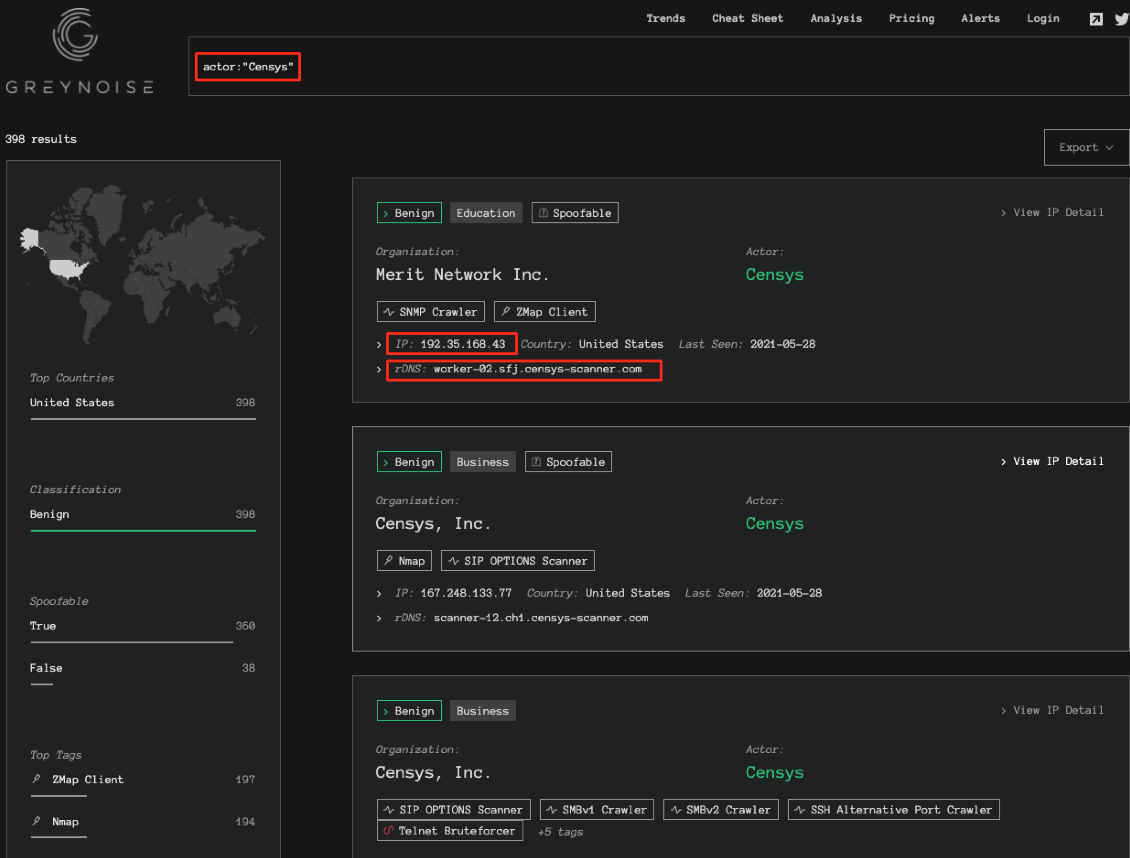
You see search engines’ IPv4 and RDNS information below. You can block BinaryEdge’s IP addresses or a more organized approach would be checking every request’s IP and RDNS data and block them accordingly.
BinaryEdge IPv4 Addresses (*.binaryedge.ninja)
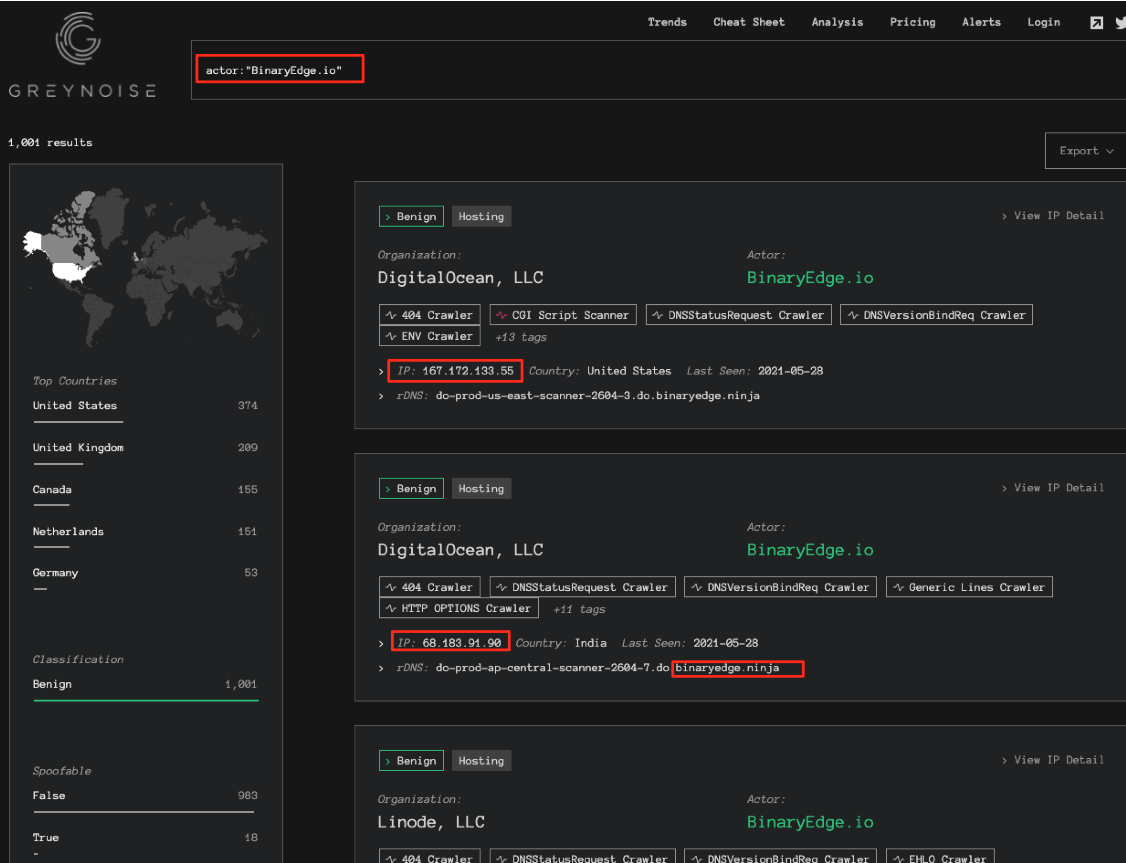
Censys IPv4 Addresses (RDNS: *.censys-scanner.com)
Useless Service Info

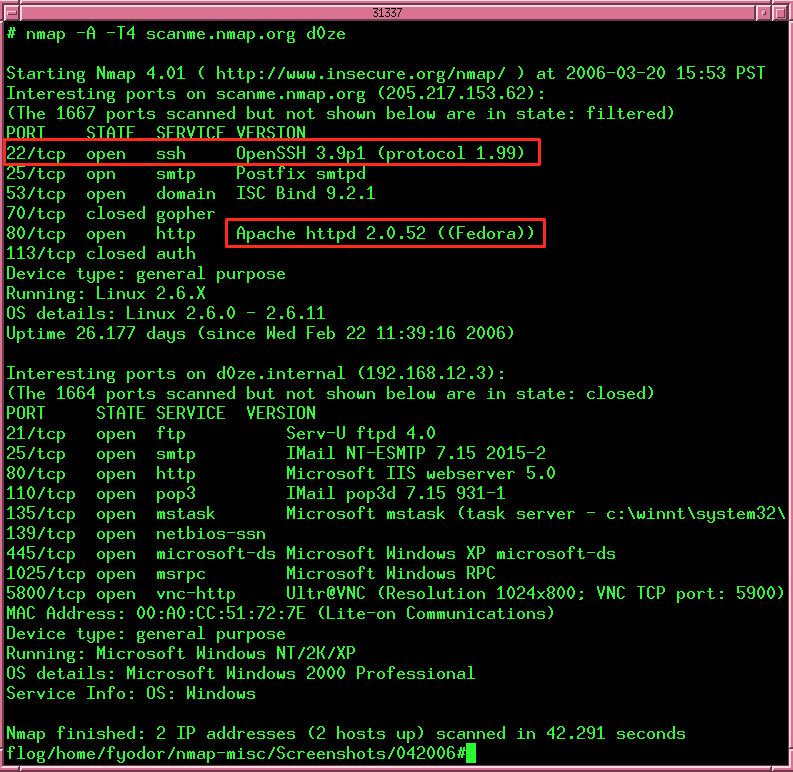
Information about digital assets that are open to the internet, version numbers, serial numbers, manufacturers are all important and could easily be used by attackers for detecting vulnerabilities in the systems and exploiting them.
Disclosure of system information helps attackers make an attack plan. Other than information that your users need, try not to disclose any information about your systems’ architecture and technologies being used.
The services that are running on default ports are usually attackers’ first focus. They will evaluate the service names, version to try to find a vulnerability, and craft service specific attack scenarios. For example, if there’s an OpenSSH 3.9p1 service running on port 22 it will be a piece of cake for attackers to find exploits. Unless you don’t have HoneyPot, that is. If the attacker wants to make sure they will use HoneyPot detection techniques.
Changing service names and versions may help to lower the attack surface, however, you shouldn’t use the default port for your services. Also removing the service names as a whole would be a solid solution and greatly reduce the attack surface.
You can check IANA’s default port list here and see if you have any open ports visible. Then you should change those to a port number that is not reserved by default.
https://www.iana.org/assignments/service-names-port-numbers/service-names-port-numbers.xhtml
DNS Data

Some of the most prestigious attack types attackers use are against DNS service. Important attacks like DNS Hijacking put systems and networks in hazardous conditions.
You can protect your domain names and FQDNs’ DNS info with DNS based firewalls such as Cloudflare. You should take note that the IP addresses you hid behind Cloudflare should not have been compromised. Meaning you should take protections such as Direct IP Restriction, SSL and search engine wise. Still, some attackers might leak your real IP behind Cloudflare. (https://www.hackread.com/cloudflare-data-leak-expose-ip-addresses-ukraine/)
General DNS Attack Types are:
- DNS DDoS Amplification
- DNS Hijacking
- DNS Tunneling
- DNS spoofing
- Man-in-the-middle with DNS
- NXDOMAIN attack
Other than these attacks there are steps you can take to further protect your DNS system and connected applications.
For example, if you’re using a system like CloudFlare, WhoIs info in your ASN data will draw attention and the IPs behind Cloudflare may be compromised.
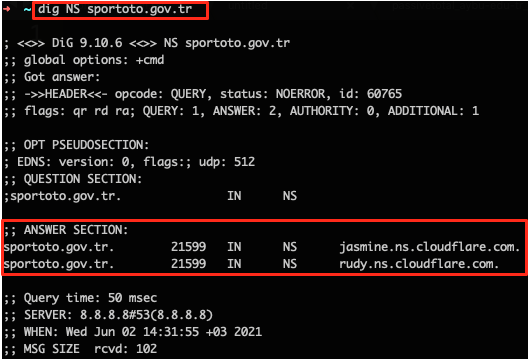
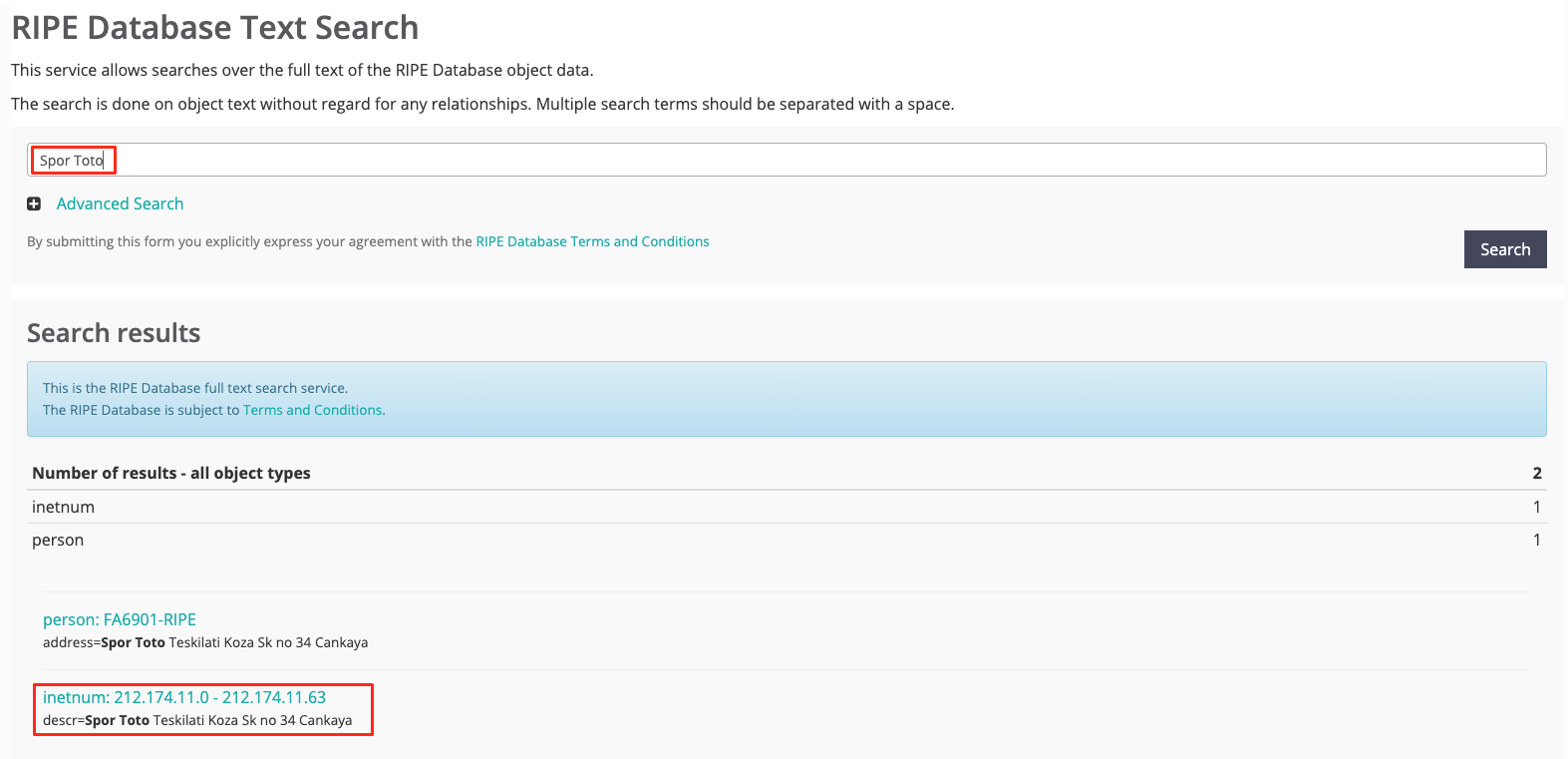
Whois Info
When you acquire a domain name there is some important information you must give to the registered organisation. Attackers might obtain some critical information about your organisation and use it pre-attack. (https://attack.mitre.org/techniques/T1596/002/)
When you’re registering domain names you shouldn’t give your technicians’, admins’ or any personnel’s name in that matter. When they quit their jobs or even still work for the same company, attackers might organize attacks such as phishing, social engineering, specially crafted for the company and/or the people.
Again, when you’re registering a domain name for the first time or even in the past WhoIs info, you are advised to not use your own DNS servers. It’s both an incremental cost and creates additional risk factors.
A DNS service that is open-source such as BIND means:
- set-up fee
- ISP bandwidth problem
- +1 network personnel
- Incremental cost
- More risk
Services like Cloudflare or AWSDNS would be better to use.
SSL/TLS
SSL/TLS vulnerabilities are one of the most common vulnerabilities today.
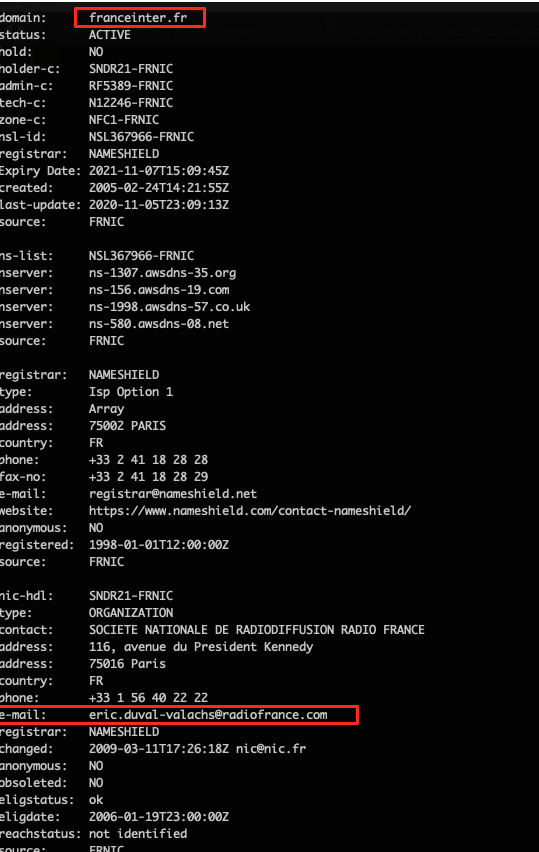
SSL/TLS has a lot of techniques used for threat hunting. One of them is SSL Transparency Logs. Distributors log info for every active SSL and threat hunters can follow these logs.
https://crt.sh/?q=tesla

You can see there had been an SSL activated for a domain before and see different FQDNs in Common Name and Matching Identities fields.
X509v3 Subject Alternative Name (https://crt.sh/?id=4501814911) field shows other FQDNs that use the certificate and other FQDNs that have been seen. Also, even the big companies sometimes forget to renew SSL/TLS certificates. This could lead to critical mistakes and vulnerabilities.
If your IP address has an HTTP Web Service for direct access, your certificate Common name will be indexed by the search engines and publicly available.
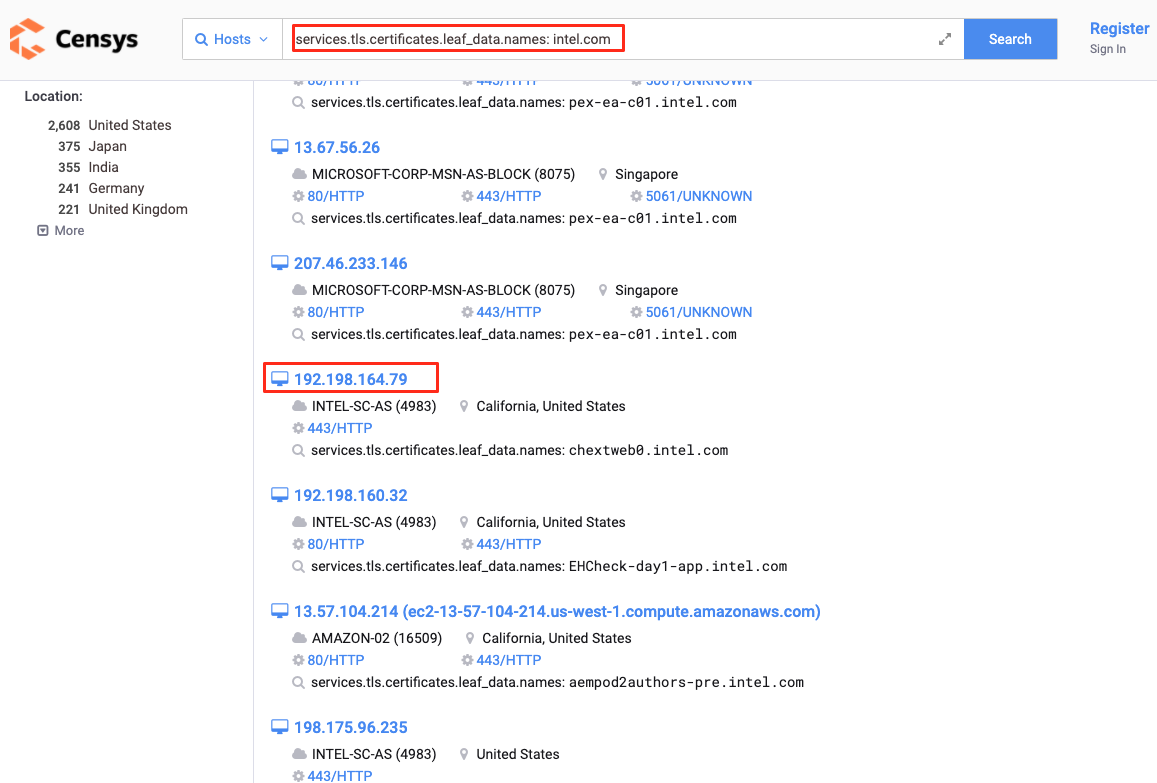
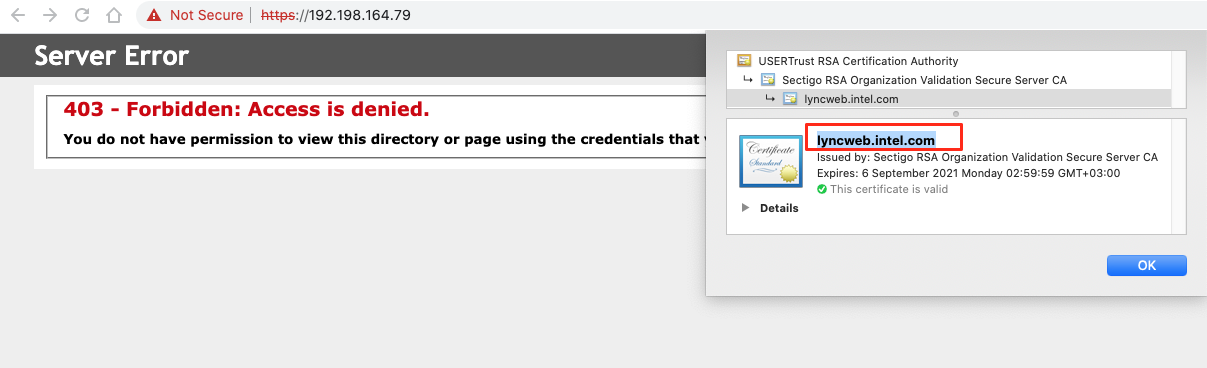
If you prevent accessing the server with an IP address you can prevent your SSL Common Name and Web Service IP address from being publicly available.
Blocking Directly Accessing from IP on Apache:
(https://serverfault.com/questions/607137/restrict-direct-ip-access-to-website)
Blocking Directly Accessing from IP on IIS:
Web Technologies and Headers

Every application, URL, Javascript, Cookie info that is on the web server is important for attackers and good starting points for information gathering. Every exposed bit of information takes attackers one step further.
We will examine how attackers can hack systems using which information, with preceding examples.
Javascript Disclosures:
Attackers can obtain Javascript keys and tokens using Nuclei’s templates and use these to access more critical information.
➜ $ nuclei -l domains.csv -t exposed-panels -t dns -t exposures -t miscellaneous -t misconfiguration -silent
[generic-tokens] [http] [info] https://conf.example.com [token=”c4iEGYaCPKbcg,PasswordConfirmation=true,password_link”:null,PasswordForPublicLink”:false,PasswordByDefault”:false,PasswordProtection”:false,Password”:false]
You can obfuscate and compress Javascript code and shouldn’t forget important keys in the code.
You can regularly check your web services that are connected to your domain names and use an open-source system that alerts you when there’s Javascript changes. (Against threats like CoinHive and JS Malwares)
Old but Gold: Basic Auth
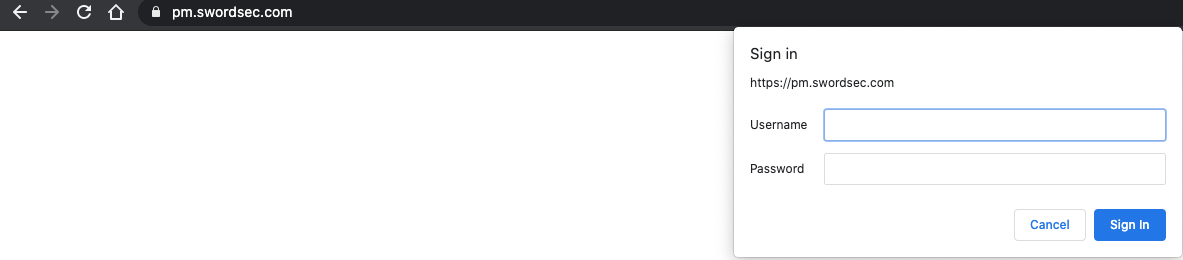
You should definitely protect your web apps with Basic Auth. It plays a key role against classic attacks and information disclosures. If you don’t use Basic Auth, attackers can access your predictable subdomains and gather further information about your web technologies and systems.
Meta Meta Meta
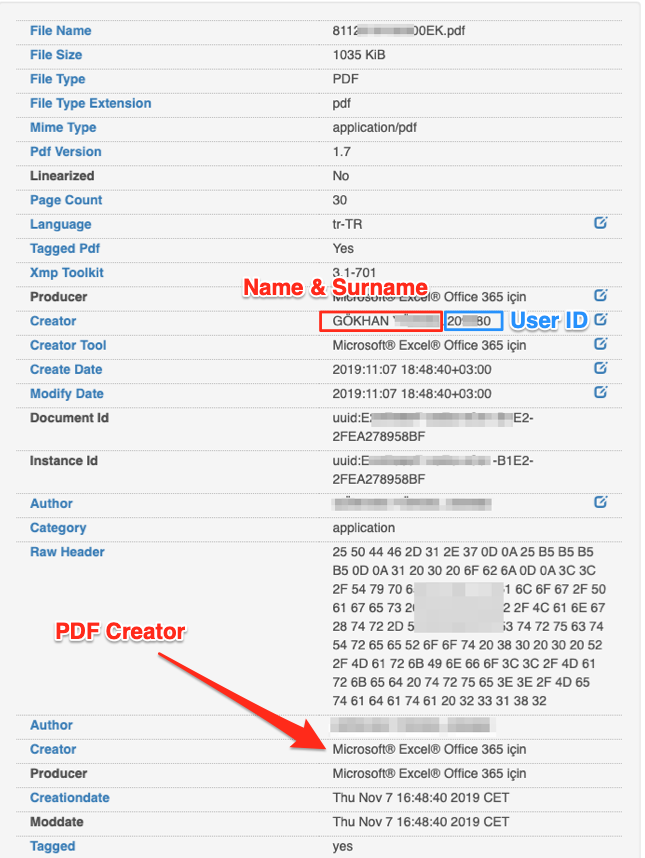
Every piece of data that has been uploaded to the internet needs its metadata altered. For example, from only metadata of a PDF file that it could be possible to gather information about the person who created the file like name and surname, technology being used and possibly information about registration number used within the company.
Cookies
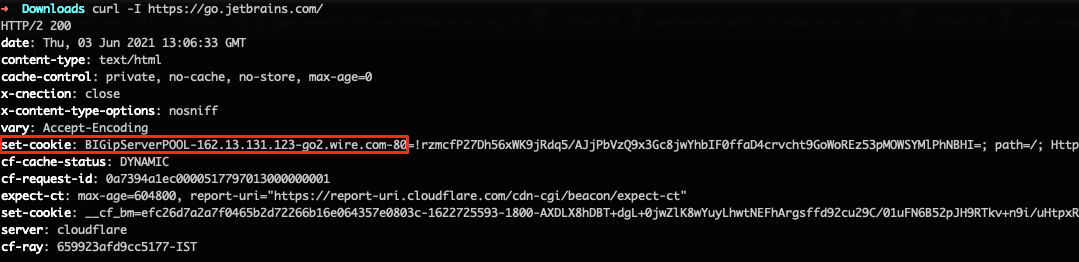
Attackers use any data leak in the cookie information. The above example shows BIGipServerPOOL disclosure in cookies at go.jetbrains.com. In this example even if they use CloudFlare, highly critical information like backend service IP, port could be disclosed.
There are a lot of services and technologies that trace cookie data regularly and historically store it. (SwordEye, RiskIQ, ZoomEye, DigitalPoint, etc). To prevent such critical leaks you should use custom, random encrypted cookie names.
For example:
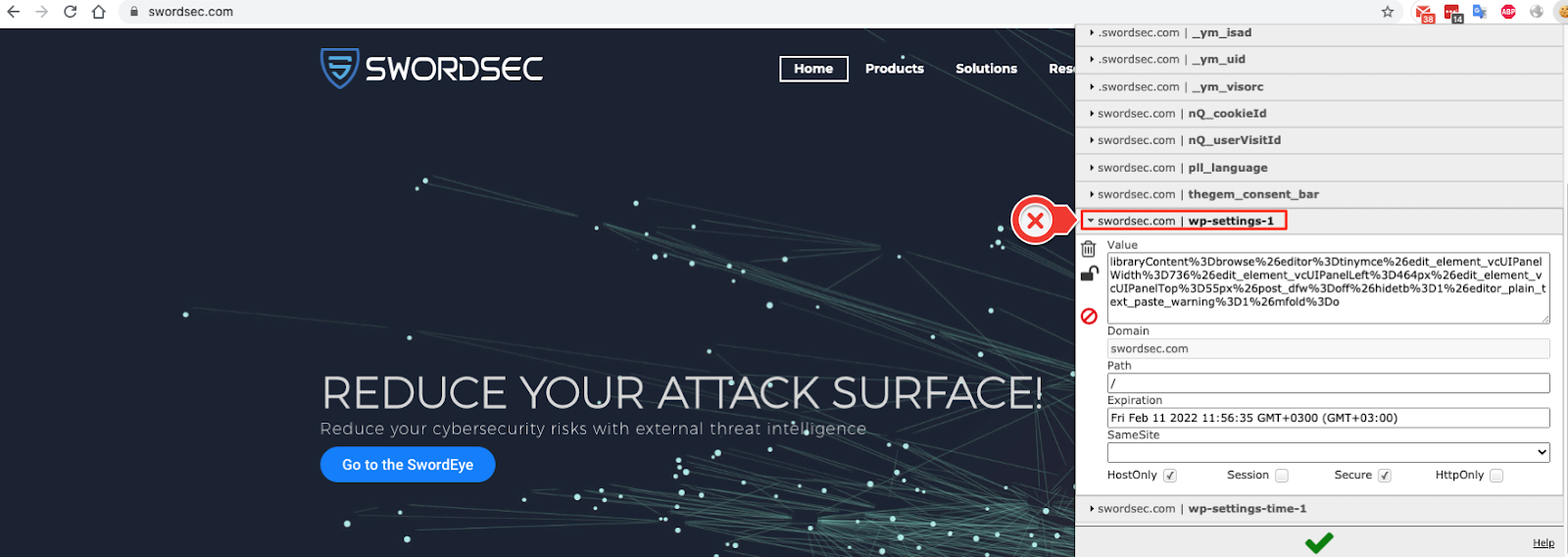
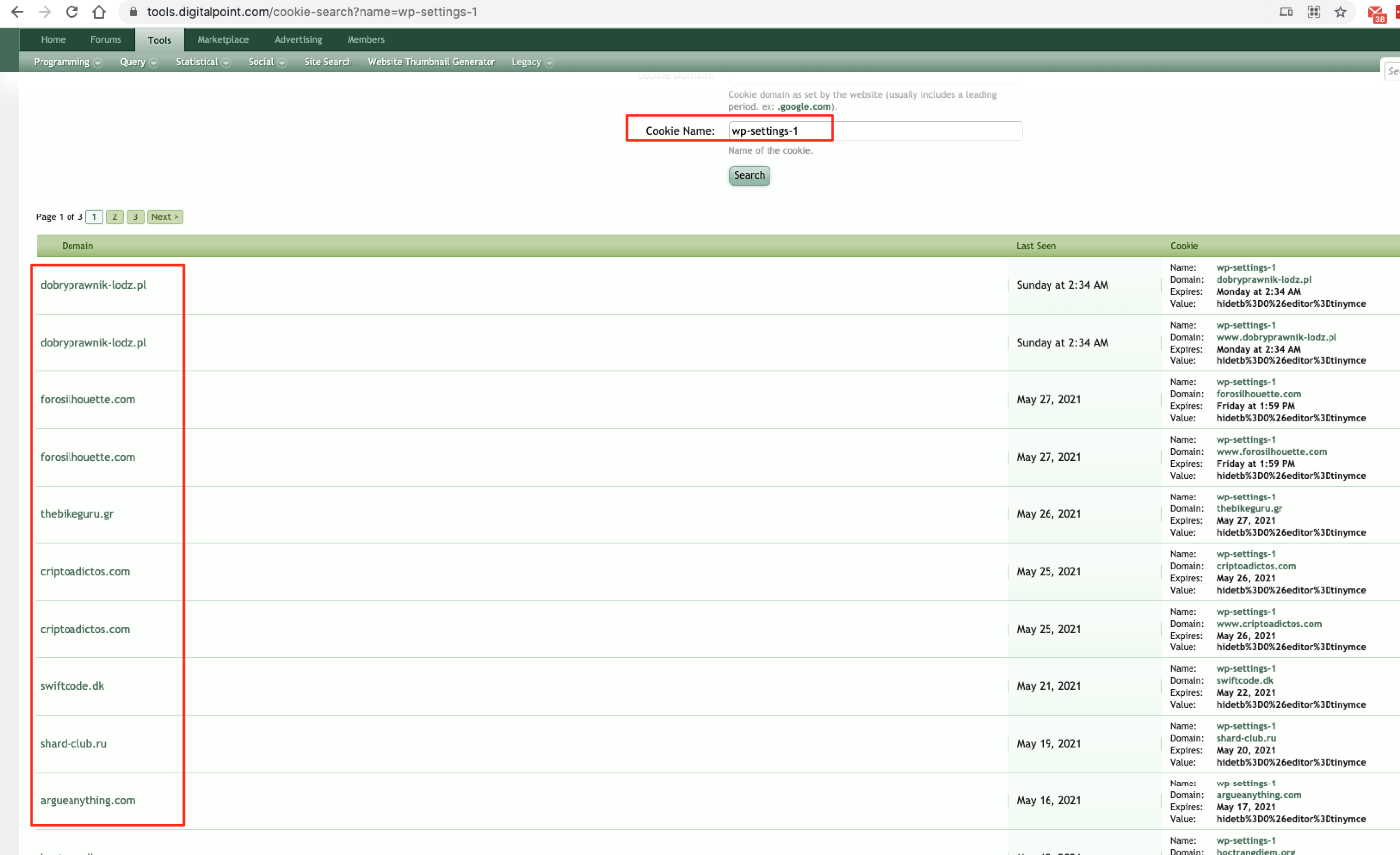
Lower Your Attack Surface

SwordEye can assess your risk threats 7/24 and suggest solutions to overcome any high severity bugs.
SwordEye can scan 38 cyber risk factors such as SSL/TLS, web technologies, Domain&WhoIs, DNS, network, IP reputation, software updates for every single digital asset that you have on the internet.
Whether it is for Penetration Testing and Red Team activities, sub-companies & supply chains’ systems, customer’s digital assets on SOC units, SwordEye is there to assess your risk factors without any setup needed.