Mobile Application Security
Introduction
With the rapid advancement of mobile technologies, the usage of mobile applications has also increased. However, as the popularity of mobile applications grows, concerns about security arise as well. The security of mobile applications is of utmost importance in terms of protecting user data, being resilient against attacks, and minimizing privacy vulnerabilities. In this article, we will focus on the key points that we need to address regarding mobile application security
Mobile Application Penetration Testing
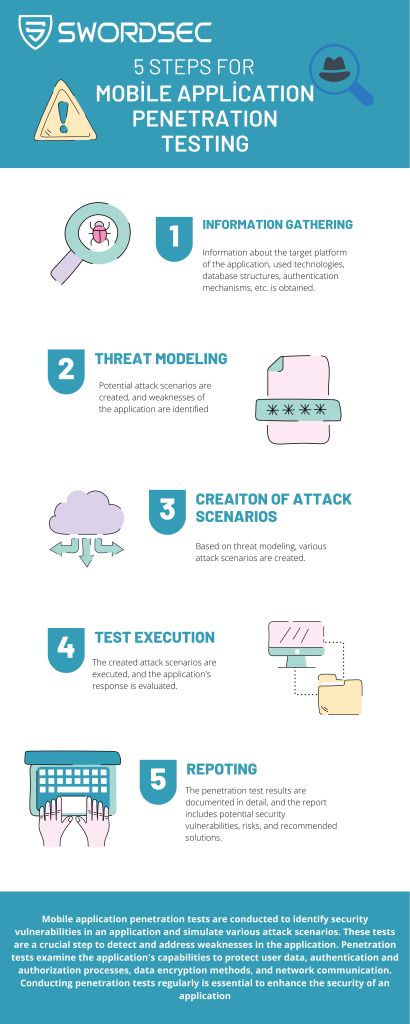
Mobile application penetration testing is a series of tests conducted to identify security vulnerabilities in an application and simulate various attack scenarios. These tests are a crucial step in detecting and addressing the weaknesses of an application. Penetration testing examines the application’s capabilities in protecting user data, authentication and authorization processes, data encryption methods, and network communications. Regularly conducting penetration tests is essential to enhance the security of an application.
Mobile application penetration testing typically includes the following steps:
Information Gathering:
Information about the target platform, used technologies, database structures, authentication mechanisms, etc., is acquired.
Threat Modeling:
Potential attack scenarios are formulated, and the application’s weak points are identified.
Creation of Attack Scenarios:
Based on the threat modeling, various attack scenarios are created.
Test Execution:
The created attack scenarios are executed, and the application’s responses are evaluated.
Reporting:
Penetration testing results are documented in detail, highlighting potential security vulnerabilities, risks, and recommended solutions.
The scope of mobile application penetration testing may vary depending on the application’s features and requirements.
Mobile application security also considers the OWASP (Open Web Application Security Project) published ‘OWASP Top 10 Mobile Application Security Risks.’ This list identifies the most common and critical mobile application security risks. Understanding these risks and taking necessary precautions accordingly is essential to enhance the security of the application
The scope of mobile application testing should encompass these risks as well. Typically, the areas it focuses on are:
User Authentication and Authorization: Aspects such as user authentication processes, password policies, and session mechanisms are examined. It is crucial for the application to resist phishing attacks by malicious users.
Data Security: The security of data within the application is evaluated. Elements such as proper data encryption and secure data storage methods are tested.
Network Communication: The security of the network communication between the application and the server is assessed. Factors like data encryption, the use of secure protocols, and firewall settings are reviewed.
Software Security: The application’s codebase and software structure are examined for potential security vulnerabilities. Secure coding principles, data validation, and handling of erroneous inputs are evaluated during this stage.
Numerous tools and frameworks are available for mobile application penetration testing. These tools are utilized to detect security vulnerabilities in the application and automate the testing process. For instance, the OWASP Mobile Security Project provides a set of open-source tools and guides used in mobile application security testing.
Secure Coding
The security of mobile applications relies on secure coding principles from start to finish. Secure coding aims to minimize security vulnerabilities during the software development and design phases. Secure coding principles encompass various aspects such as proper validation of user inputs, secure database operations, and secure handling of externally sourced data. Adherence to coding standards helps prevent security vulnerabilities and enhances the application’s security.
Best Practices
Following best practices in mobile application security is crucial to enhance the security of your application. Adhering to up-to-date security standards and best practices makes your application more resilient against attacks. This may involve regular security updates and patches. Additionally, being transparent about protecting your users’ data and clearly communicating privacy policies is essential.
Conclusion
Mobile application security is of paramount importance to safeguard user data privacy and ensure the trustworthiness of the application. By conducting penetration tests, adopting secure coding techniques, and implementing best practices, you can elevate the security level of your mobile application. Continuously focusing on mobile application security and persistently pursuing efforts in this area are essential to earn users’ trust and build a resilient application against cyber threats.
For those who want to learn more about Mobile Application Pentesting, they can access detailed information by checking out the following resource. To explore the relevant guide, click on this link.