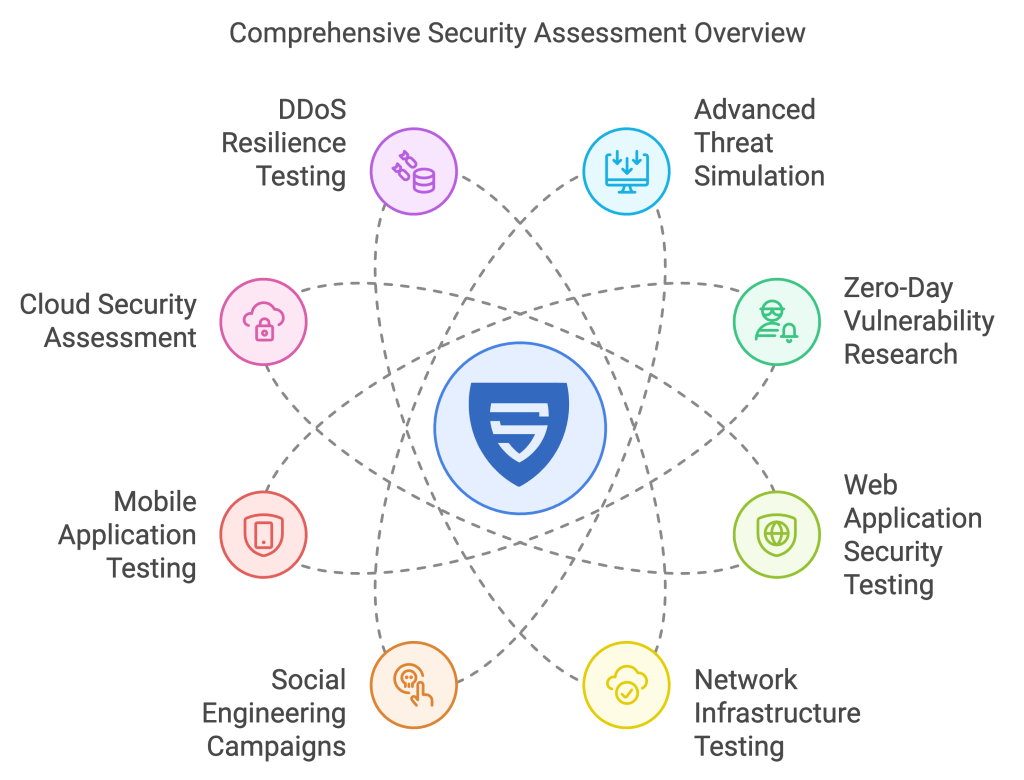
SwordSec’s penetration testing and red teaming services empower you to identify and close gaps in your security posture. Our comprehensive approach dives into every layer of your infrastructure, from cloud and mobile applications to your network’s resilience against DDoS attacks.
Key Offerings:
- DDoS Resilience Testing: Measure your defenses against high-volume attacks.
- Advanced Threat Simulation: Experience realistic adversary tactics to test your security boundaries.
- Zero-Day Vulnerability Research: Stay protected against emerging threats.
- Web and Mobile Security Testing: Fortify your applications to safeguard user trust.
- Social Engineering Campaigns: Strengthen the human side of your security.
Secure your digital environment with SwordSec. Scroll down to explore the full range of our services.
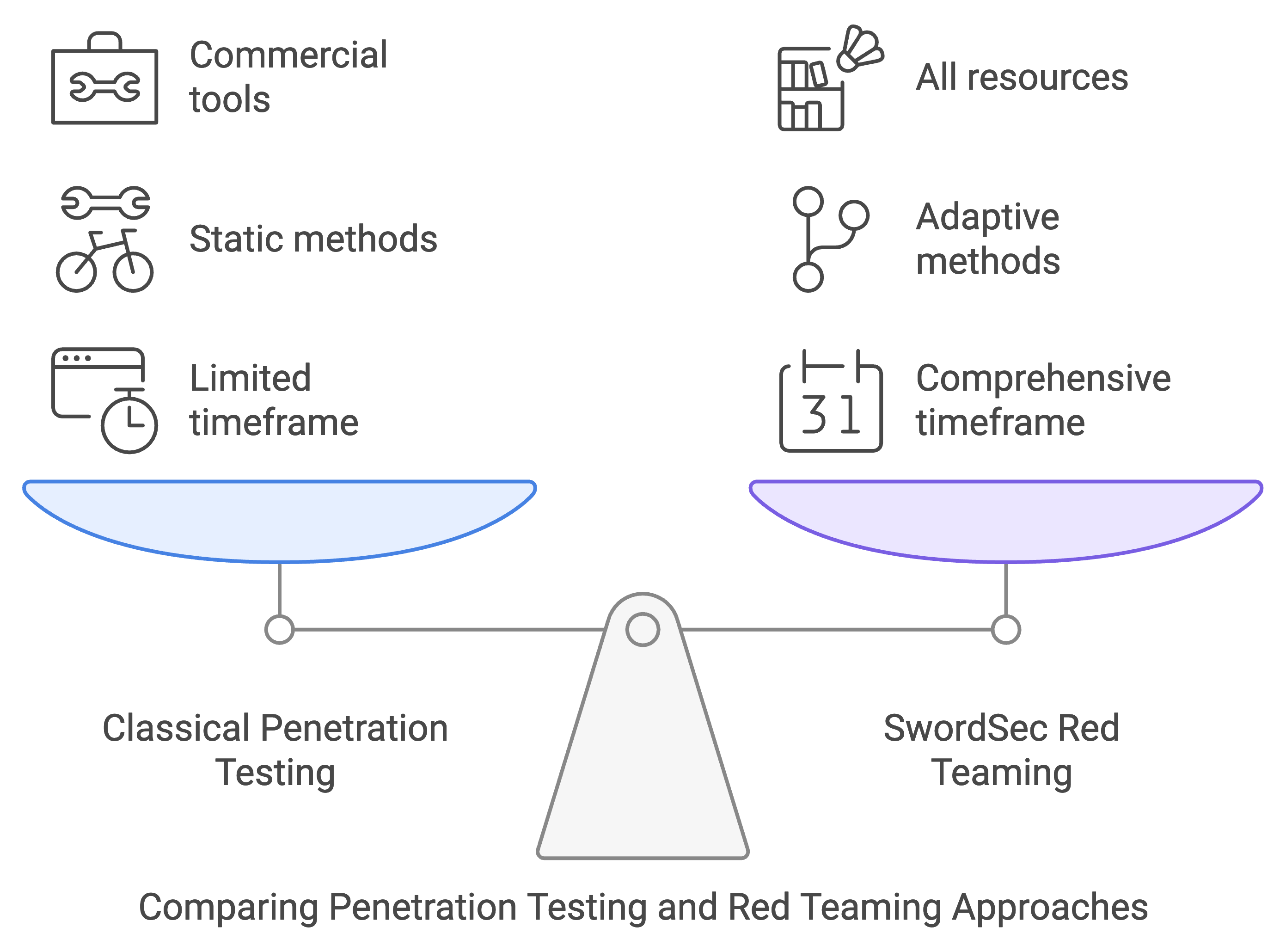
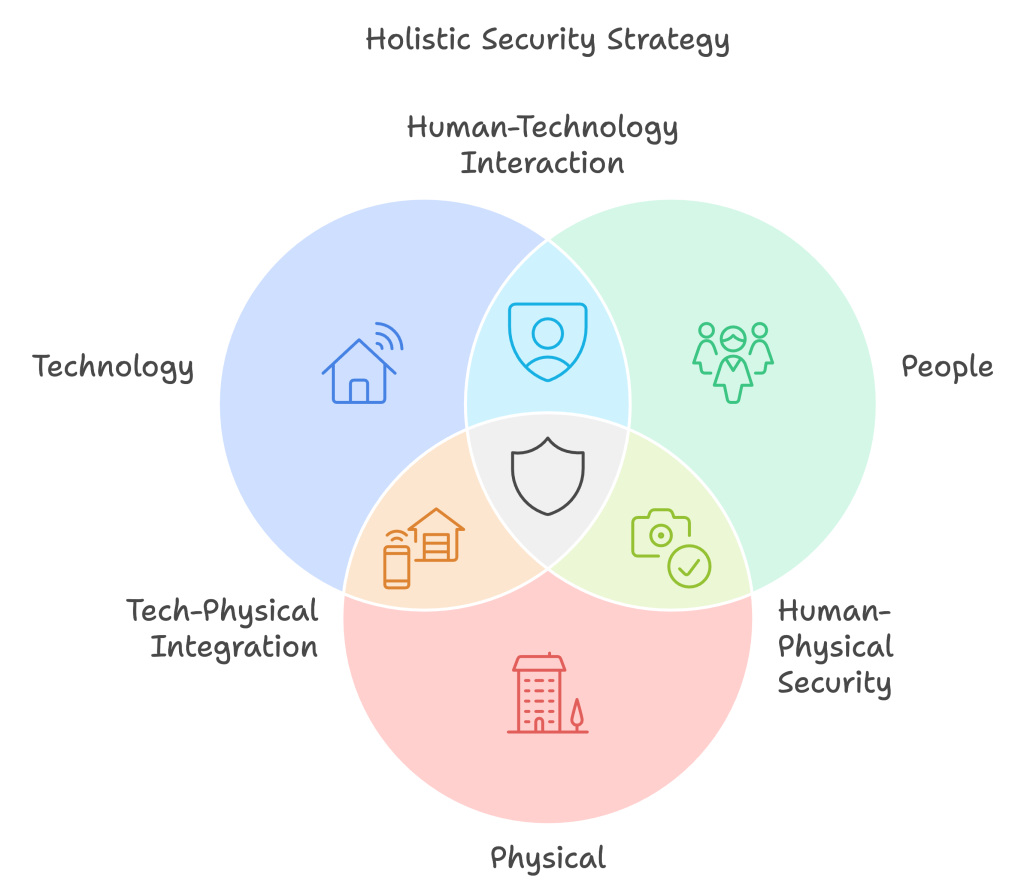
Red Teaming service and Penetration Testing can often be confused. Both of them have the same goal, however, there are differences in terms of the application. Red teaming is a more extensive test that tests human factors, physical products and such… Red Teaming tests are applied only within the knowledge of managers and some key workers.
– Simulation of Advanced Persistent Threat (APT) tactics
– Nation-state level attack methodologies
– Multi-vector attack scenarios
– Custom malware simulation
– Data exfiltration attempts
– Defense evasion techniques testing
– Persistence mechanism validation
– Custom exploit development
– Advanced vulnerability discovery
– Application security research
– Protocol analysis
– Binary exploitation
– Firmware security testing
– Cloud infrastructure vulnerability assessment
– OWASP Top 10 vulnerability assessment
– Business logic flaw detection
– Authentication bypass testing
– Session management testing
– API security assessment
– XML/JSON injection testing
– GraphQL security testing
– File upload vulnerability testing
– CSRF/XSS vulnerability detection
– SQL injection assessment
– External/Internal network penetration testing
– Wireless network security assessment
– VPN security testing
– Firewall rule review
– Network segmentation validation
– Router/Switch configuration review
– VLAN hopping attempts
– Man-in-the-middle attack simulation
– DNS security assessment
– Phishing campaign simulation
– Spear-phishing exercises
– Vishing (voice phishing) tests
– Physical social engineering
– USB drop testing
– Tailgating attempts
– Pretexting scenarios
– Email security assessment
– Android/iOS application security testing
– Mobile API security assessment
– Local data storage security
– Network communication security
– Binary analysis
– Runtime manipulation testing
– Third-party library analysis
– SSL/TLS implementation review
– AWS/Azure/GCP security review
– Container security testing
– Kubernetes cluster assessment
– Serverless function security
– Cloud configuration review
– IAM policy assessment
– Storage bucket security
– Cloud network security
– Application layer (Layer 7) testing
– Network layer stress testing
– Protocol abuse testing
– Volumetric attack simulation
– TCP state exhaustion tests
– Infrastructure resilience assessment
– DDoS mitigation validation
– Scope of Potential Breach:
– Data access assessment
– Privilege escalation paths
– Lateral movement opportunities
– Persistence establishment
– Command & Control channels
– Deliverables Include:
– Detailed technical findings
– Risk-rated vulnerabilities
– Executive summary
– Strategic recommendations
– Tactical remediation steps
– Prioritized action items
– Future security roadmap
– NIST Framework alignment
– ISO 27001 requirements
– GDPR compliance assessment
– PCI DSS validation
– HIPAA security evaluation
– SOC 2 control testing
– Industry-specific regulations
– IoT device security testing
– SCADA/ICS security assessment
– Embedded system testing
– Source code review
– Architecture review
– Third-party vendor assessment
– Supply chain security review