In a continuously growing internet environment, new threats are emerged every day. There are many different types of these threats, and security vulnerabilities, which are perhaps the most important ones, are increasing day after day. NVD (National Vulnerability Database), which is one of the most popular vulnerability databases, currently has more than 148000 registered vulnerabilities.
Table of Contents
What is a Vulnerability? Why Does It Occur?
Vulnerability is a name given to a weakness in a software that can be exploited by an attacker for his/her own benefit. These vulnerabilities are used to target the host where the software is installed, and as a result of a successful attack, attackers have access to the host’s main memory and storage. That way, an environment is prepared for the installation of malicious software, information theft and information change. There are many reasons why vulnerabilities occur. The complexity and large of a system, make it prone to incorrect coding. Therefore, bugs are more common in larger software. Using well-known software increases familiarity with that code. Therefore, an attacker can easily find a vulnerability in a code they already know. As a software’s dependency to the internet increases, the number of its vulnerabilities also increases. Not checking user input can also cause vulnerabilities. To summarize briefly, coding and installation -configuration- errors are the main causes of vulnerabilities.
The Most Commonly Used Vulnerabilities by Attackers
Records are collected in vulnerability databases as vulnerabilities and their information emerge. According to the information obtained from these databases and cyber security research, the most commonly used vulnerabilities in 2020 are listed as follows:
CVE-2017-11882 (Microsoft Office Memory Corruption Vulnerability)
This vulnerability, which was published on NVD on November 14, 2017, is a vulnerability that emerged in Microsoft Office products. The vulnerability, by causing a corruption in the machine’s memory, allows the attacker to execute malicious code.
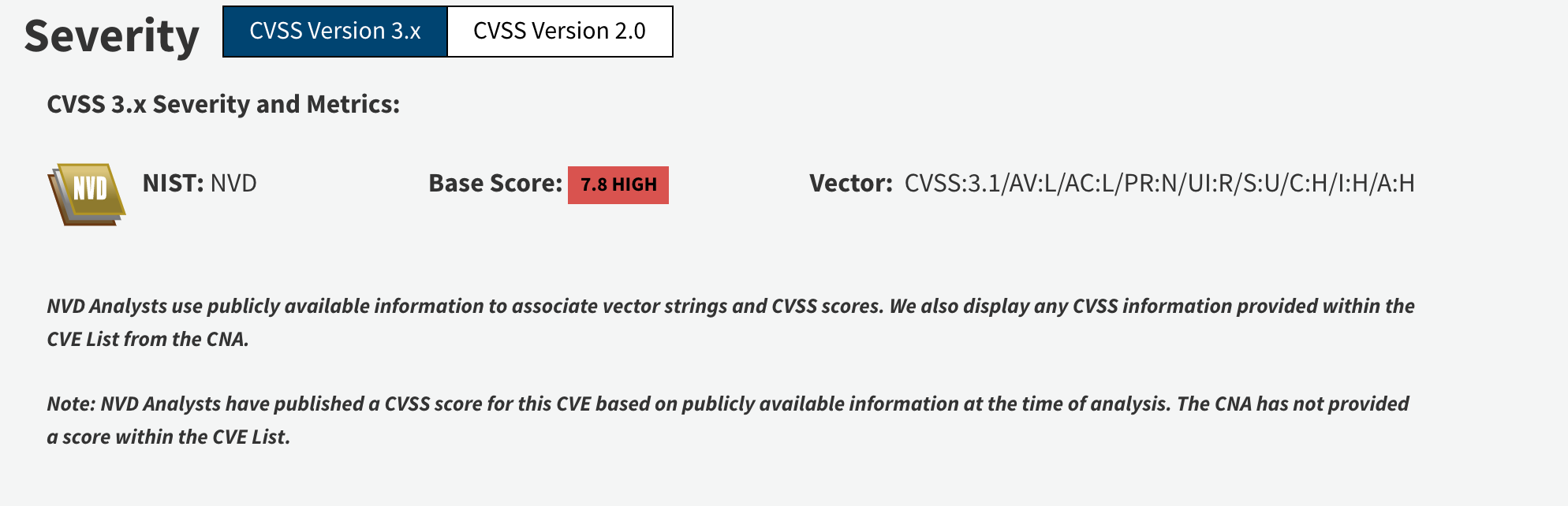
CVE : https://nvd.nist.gov/vuln/detail/CVE-2017-11882
CVE-2017-0199 (Microsoft Office/WordPad Remote Code Execution Vulnerability w/Windows API)
This vulnerability, which was published on NVD on April 12, 2017, is a vulnerability that emerged in Microsoft Office and Windows products. The vulnerability allows attackers to execute code through a maliciously crafted document.
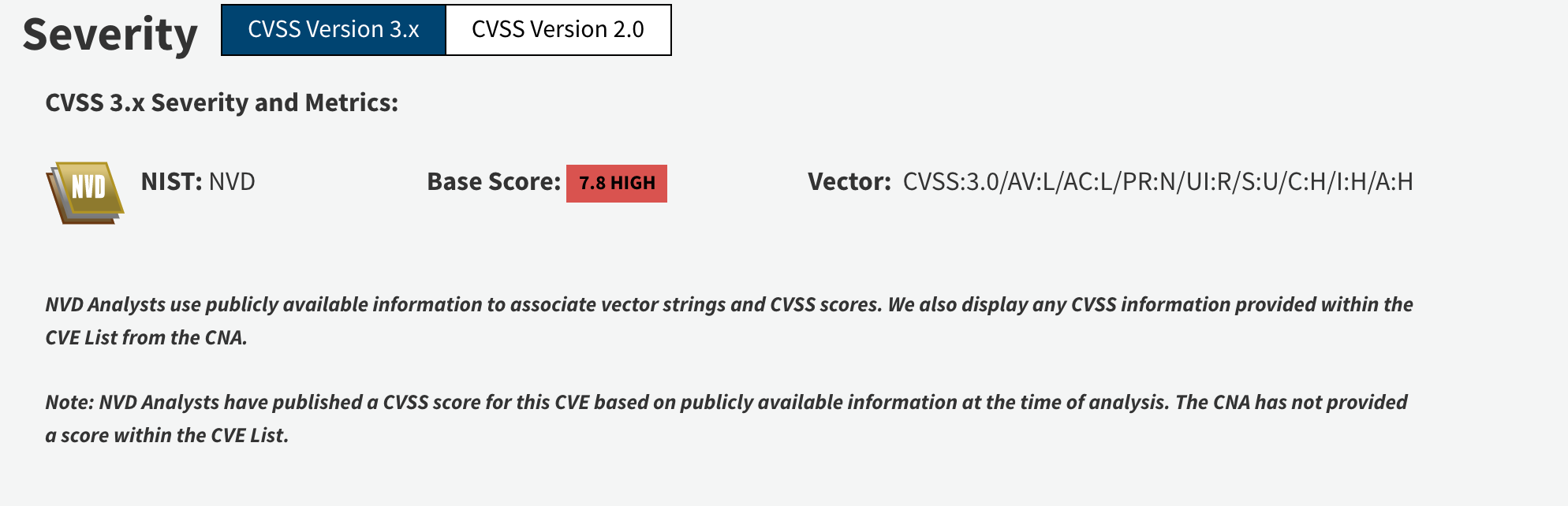
CVE : https://nvd.nist.gov/vuln/detail/CVE-2017-0199
CVE-2017-5638
This vulnerability, published on NVD on March 10, 2017, is a vulnerability in the Jakarta Multipart parser of Apache Struts products. Through the vulnerability, attackers can run commands on the machine using an HTTP header.
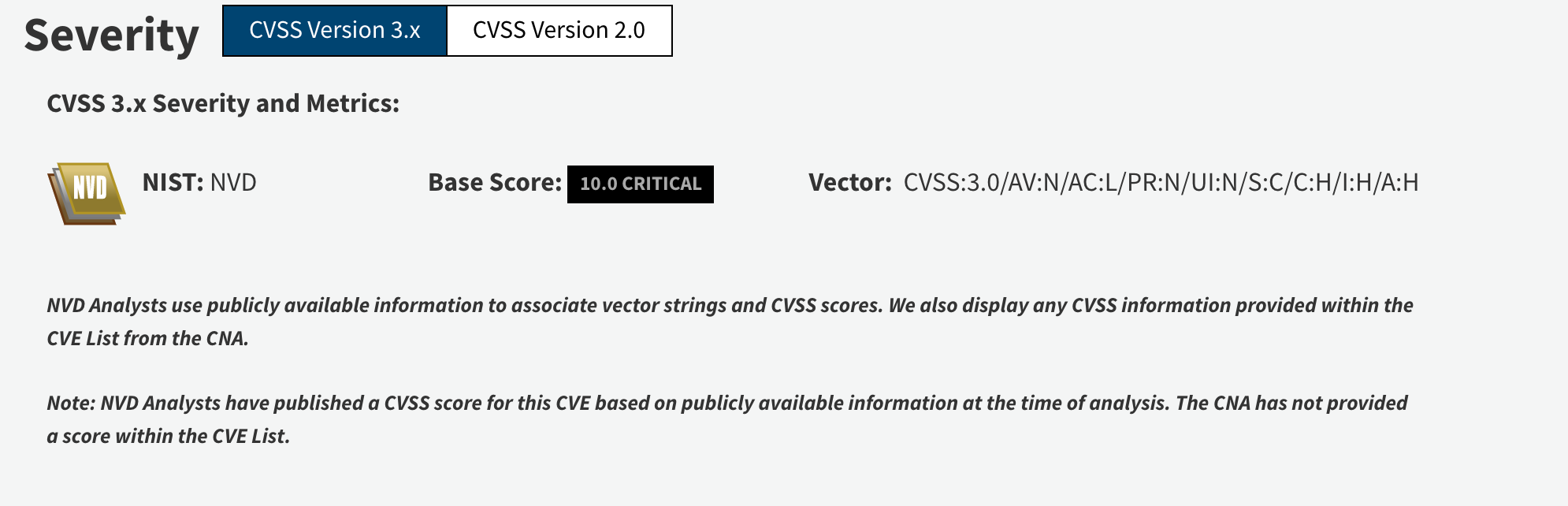
CVE : https://nvd.nist.gov/vuln/detail/CVE-2017-5638
CVE-2012-0158 (MSCOMCTL.OCX RCE Vulnerability)
This vulnerability, which was published on NVD on April 10, 2012, is a vulnerability that emerged in Microsoft products. Attackers who want to exploit the vulnerability can run code by corrupting the system state through a malicious web page, Office document or RTF document.
CVE : https://nvd.nist.gov/vuln/detail/CVE-2012-0158
CVE-2019-0604 (Microsoft SharePoint Remote Code Execution Vulnerability)
This vulnerability, which was published on NVD on April 10, 2012, is a vulnerability that emerged in Microsoft products. Attackers who want to exploit the vulnerability can run code by corrupting the system state through a malicious web page, Office document or RTF document.
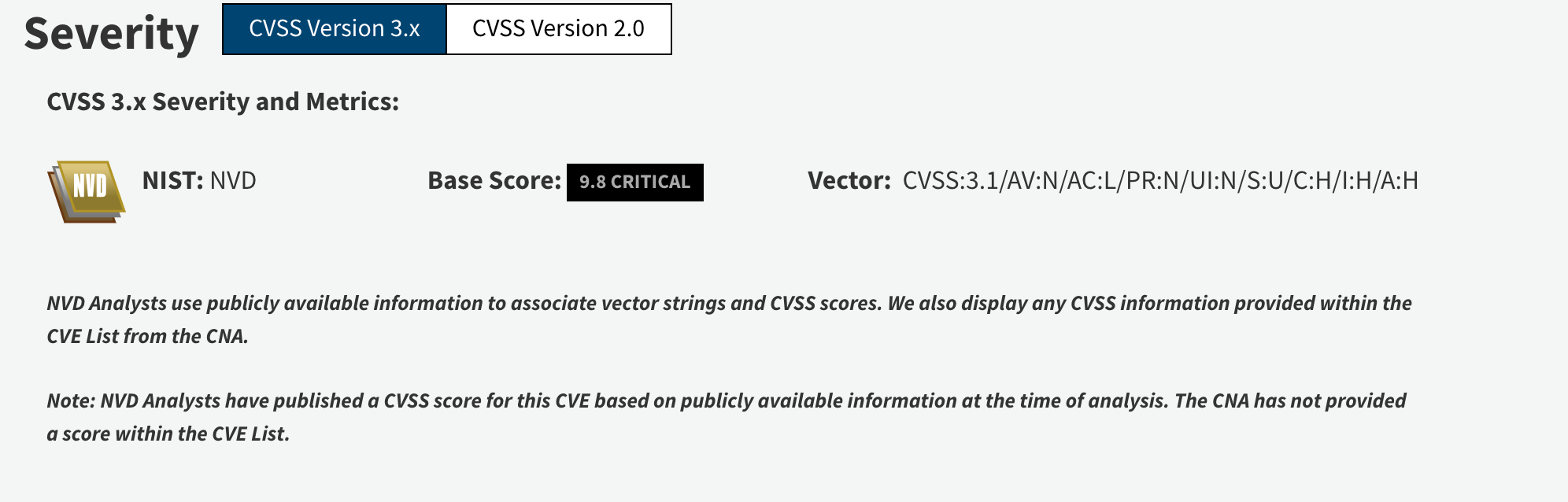
CVE : https://nvd.nist.gov/vuln/detail/CVE-2019-0604
CVE-2017-0143 (EternalBlue)
This vulnerability, published on NVD on March 16, 2017, is a vulnerability that emerged in Microsoft Windows products. It allows attackers to run code remotely through packages prepared by them.
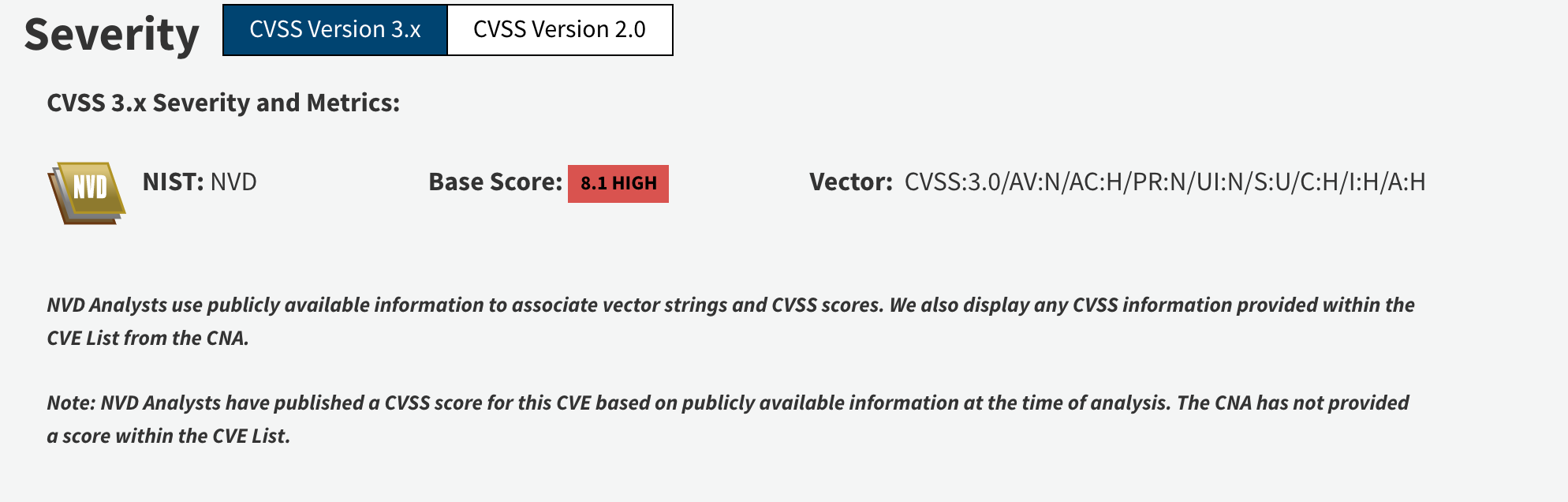
CVE : https://nvd.nist.gov/vuln/detail/CVE-2017-0143
CVE-2018-4878
This vulnerability, published on NVD on February 6, 2018, is a vulnerability in the Adobe Flash Player product. It allows the attacker to run code on the system after a successful attack.
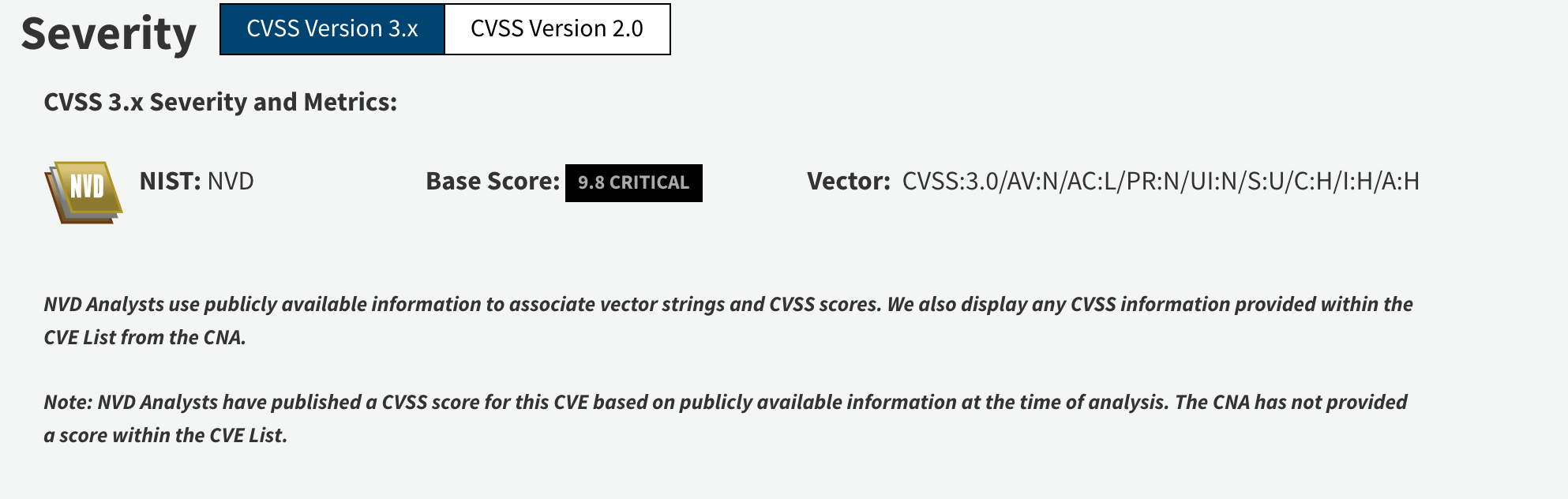
CVE : https://nvd.nist.gov/vuln/detail/CVE-2018-4878
CVE-2017-8759 (.NET Framework Remote Code Execution Vulnerability)
This vulnerability, published on NVD on September 12, 2017, is a vulnerability in the Microsoft .NET Framework product. It allows the attacker to run commands on the machine through a malicious document or program.
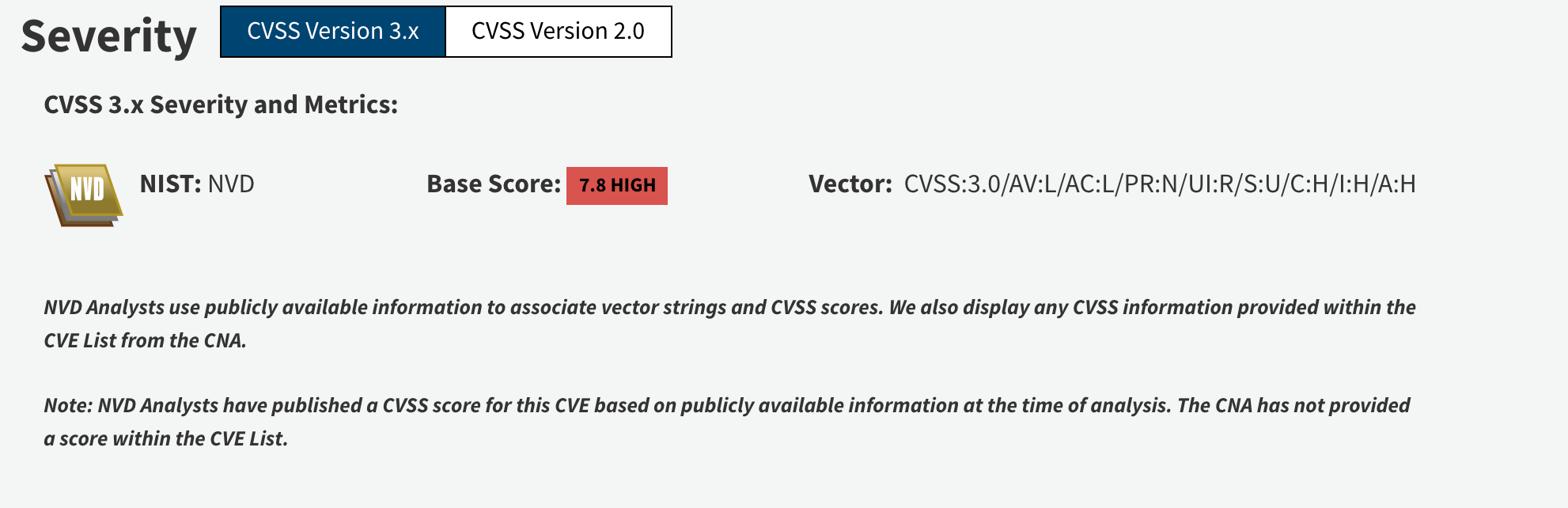
CVE : https://nvd.nist.gov/vuln/detail/CVE-2017-8759
CVE-2015-1641 (Microsoft Office Memory Corruption Vulnerability)
This vulnerability, published on NVD on April 14, 2015, is a vulnerability that emerged in Microsoft Office products. It allows attackers to execute code remotely through a malicious RTF document.
CVE : https://nvd.nist.gov/vuln/detail/CVE-2015-1641
CVE-2018-7600
This vulnerability, published on NVD on March 29, 2018, is a vulnerability in the Drupal product. It allows attackers to run malicious code remotely on machines with default configuration.
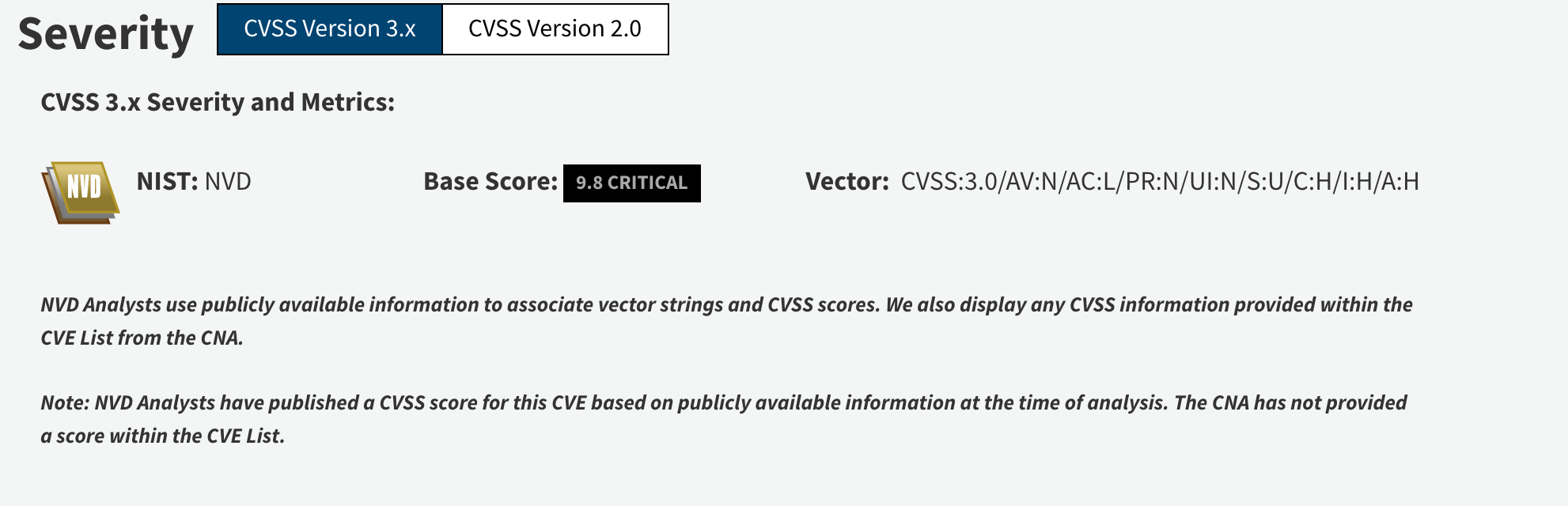
CVE : https://nvd.nist.gov/vuln/detail/CVE-2018-7600
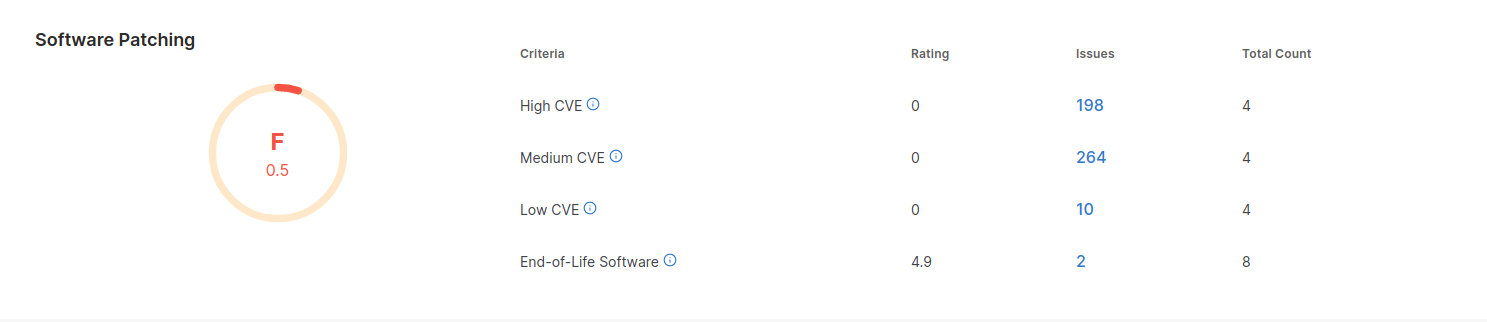
Why SwordEye For Vulnerability Monitoring?

SwordEye Attack Surface Mapping gives your organization risk scores by monitoring your digital assets and external threats without the need of any configuration. Software Patching category and the applications belonging to all your assets are monitored 24/7 with a risk algorithm. The CVEs of your applications are extracted. That way, you will continue to use your applications in up-to-date and secure way. It is possible to monitor the vulnerabilities discovered on your system currently, without the need for installation with SwordEye.