Web Application Security
Introduction
Web applications have rapidly become an integral part of the ever-expanding digital world. However, the security of web applications holds paramount importance in safeguarding user data and sensitive information. OWASP (Open Web Application Security Project) Top 10 stands out as a guide that lists the most common and dangerous security vulnerabilities in web applications. In this article, we will delve into OWASP Top 10 vulnerabilities, secure coding principles, web application security
testing, and best practices
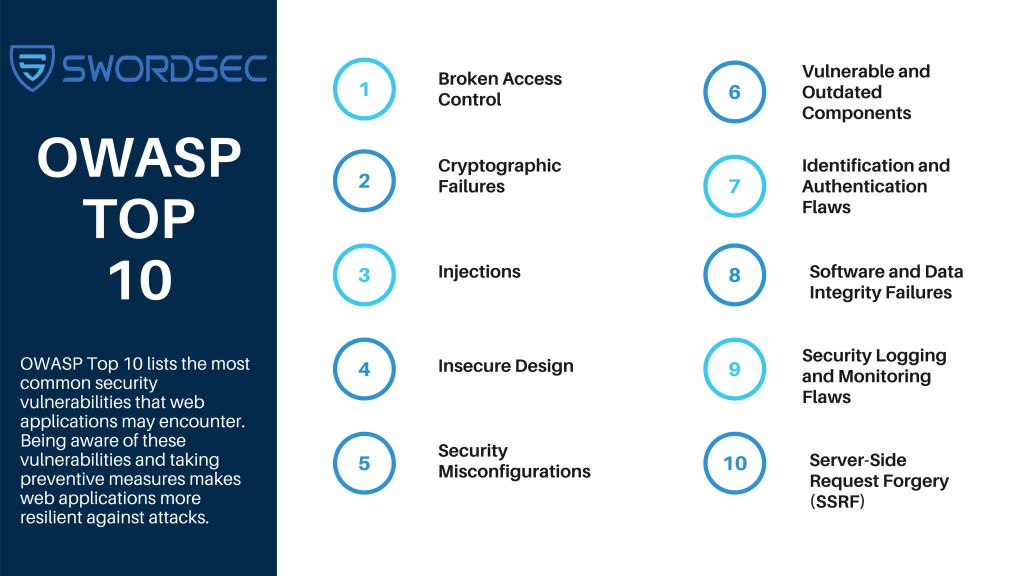
OWASP Top 10 Web Application Security Vulnerabilities:
OWASP Top 10 lists the most common security vulnerabilities that web applications may encounter. Being aware of and addressing these vulnerabilities helps web applications become more resilient against attacks. Here are the OWASP Top 10 web application security vulnerabilities
A01:2021 Broken Access Control:
Broken Access Control is the lack of sufficient authentication controls for users attempting to access restricted resources. This security vulnerability can occur when an application or system fails to implement appropriate access restrictions, such as passwords, user roles, or permissions.
A02:2021 Cryptographic Failures:
This is a critical web application security vulnerability. The data, whether at rest or in transit, contains sensitive information that requires additional security measures. Companies governed by regulations such as CCPA, PCI-DSS, HIPAA, GDPR, etc., should consider this issue of utmost importance.
Some examples of cryptographic failures include the use of outdated padding techniques, insufficient randomness in cryptographic operations, vulnerable side-channel data or cryptographic warnings, storing information in plain text, inability to use effective and modern encryption algorithms, improper management of keys, and so forth.
A03:2021 Injection:
An attacker can potentially exploit injection security vulnerabilities by injecting unauthorized data into an interpreter through SQL, NoSQL, OS, or LDAP methods. This attack vector allows the attacker to deceive the interpreter and force the application to execute unexpected commands or gain unauthorized access to data, enabling malicious data injection to perform unwanted actions
A04:2021 Insecure Design:
When a design or architectural flaw leads to a security vulnerability that a malicious attacker can exploit, it is referred to as insecure design in online applications. This scenario is commonly termed as missing or inadequate/weak control design.
A05:2021 Security Misconfigurations:
Incorrect security configurations occur when the security controls/settings of an application are not properly defined, configured, or implemented, or when default values are left unprotected. This exposes the application to potential risks.
A06:2021 Vulnerable and Outdated Components:
Software frameworks or components that contain security vulnerabilities or are no longer supported are referred to as ‘vulnerable and outdated components,’ making them susceptible to attacks. Many modern distributed web applications utilize open-source libraries and frameworks as part of their designs. Any piece with a known security vulnerability can become a weak point that jeopardizes the security of the entire application
A07:2021 Identification and Authentication Failures:
Cybercriminals can steal and exploit login credentials, private keys, or session identifiers if applications mishandle session management or user authentication. This allows them to impersonate other individuals temporarily or permanently, including their real identities and privileges. Such a security vulnerability severely jeopardizes the security of the application and the resources it accesses, while also posing a significant risk to other resources and devices connected to the network.
A08:2021 Software and Data Integrity Failures:
Software and data integrity issues arise when infrastructure and code lack protection against data security breaches. Examples include applications that use untrusted sources, pools, or content delivery networks (CDNs), as well as plugins, libraries, or modules.
A09:2021 Insufficient Logging and Monitoring:
The lack of monitoring in the presence of suspicious actions and occurrences can expand gaps over time, leading to security breaches going unnoticed for longer periods than they would with proper logging. This OWASP Top 10 2021 section aims to aid in identifying, reporting, and resolving recent breaches.
A10:2021 Server-Side Request Forgery (SSRF):
Server-Side Request Forgery or SSRF is a web security vulnerability that allows an attacker to force a server-side application to make HTTP requests to any chosen domain. This category illustrates a scenario where the security community is informed about something significant despite it not being displayed in the data.
Secure Coding:
Secure coding is a critical factor in making web applications resistant to security vulnerabilities. Secure coding principles include following best practices during the application development process to prevent security flaws.
As an example, the following actions can be taken:
- Implement access controls correctly and securely.
- Validate and filter user-provided input data.
- Encrypt sensitive data.
- Use secure data validation and output encoding techniques.
- Avoid security pitfalls that could lead to vulnerabilities, such as SQL injection or XSS.
Tools for Web Application Security Testing:
- Burp Suite: An essential tool for web application security testing, Burp Suite provides a comprehensive platform. It allows capturing web traffic through browsers, making modifications to web page requests, and providing automation. Burp Suite can also be used for detailed enumeration and analysis of web applications.
- Postman: While not a security tool per se, Postman is a highly useful REST client for testing backend APIs. This tool facilitates API security testing and is frequently preferred by security researchers.
Discovery phase is crucial in web application security testing, especially when conducting “Black Box” tests where no scope is provided. In such tests, you need to identify and explore the attack surface on your own. Here are some discovery tools we can recommend:
- OWASP Amass
- SubBrute
- Knock
- DNSRecon
- Sublist3r
- Aquatone
- Subfinder
Of course, this list only includes some examples, and you can find more detailed information through this link.
Web Application Security Testing:
Web application security testing is an important step to identify and address security vulnerabilities in the application. Below are some methods of web application security testing:
- Penetration Testing: Simulating real attacks to detect security vulnerabilities.
- Vulnerability Scanning: Using automated tools to detect known security vulnerabilities.
- Code Review: Reviewing the web application’s source code to identify security vulnerabilities.
- Application Security Audits: Conducting comprehensive audits to assess the overall security status.
Recommended Actions:
Best practices for web application security should be followed as an ongoing process. Here are some best practices:
- Regularly conduct and update security tests.
- Follow security standards and guidelines like OWASP Top 10.
- Adhere to secure coding principles and perform security audits.
- Evaluate and update third-party components for security.
- Provide user education and awareness.
Conclusion:
Web application security is of paramount importance for safeguarding user data and sensitive information. The OWASP Top 10 web application security vulnerabilities provide guidance in this regard. Secure coding principles and web application security testing are crucial steps to enhance application security. Following best practices makes web applications more resilient to attacks and instills user trust