What is DDoS?
DDoS (Distributed Denial of Service) is a cyberattack that prevents regular users from accessing a server, service, or network by filling it with an excessive amount of fake traffic. Unlike DoS attacks, which are launched from a single device, DDoS attacks are carried out simultaneously from many different sources. These attacks, which aim to disrupt or completely halt network services, can cause significant financial and operational harm to businesses.
 Purposes of DDoS Attacks
Purposes of DDoS Attacks
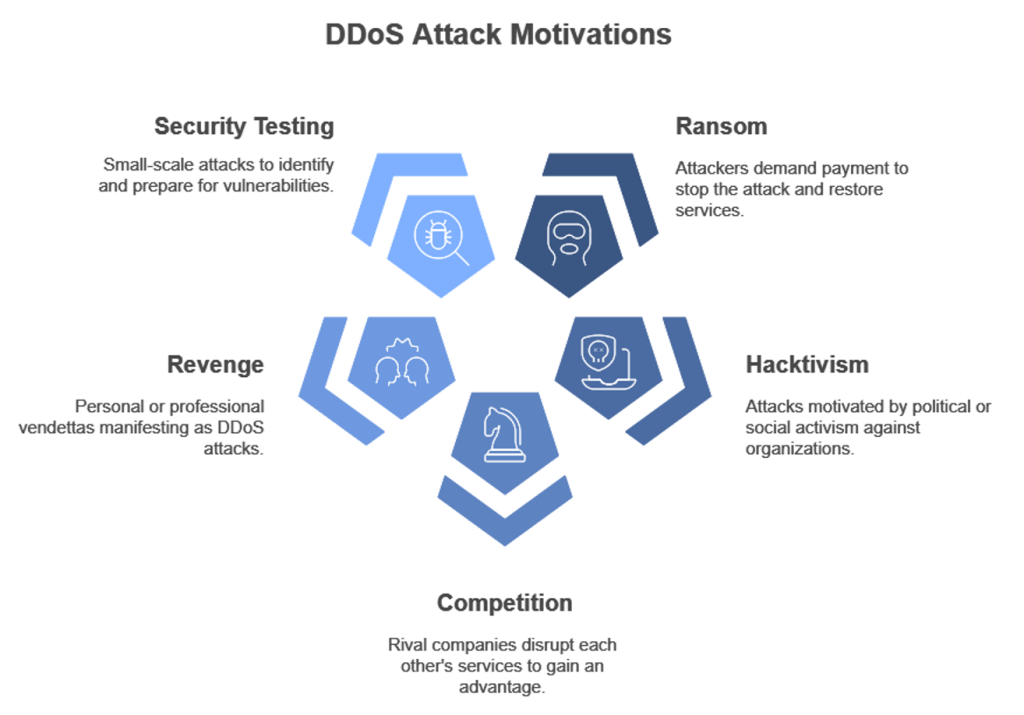
DDoS attacks can be carried out for different motivations:
- Ransom (RDoS): Attackers demand a ransom to reactivate the system.
- Hacktivism: Attacks against an organization for political or social reasons.
- Competition Among Rivals: Competing companies may use DDoS attacks to disrupt the services of their competitors.
- Revenge: Attacks carried out for personal or professional reasons.
- Security Testing: Small-scale attacks to test system vulnerabilities and prepare for larger attacks in the future.
 Working Principle of DDoS Attacks
Working Principle of DDoS Attacks
DDoS attacks are carried out through botnet networks made up of compromised devices, or “zombies,” controlled by the attacker. These botnets consist of virus-infected computers or IoT (Internet of Things) devices. Each device in the botnet sends fake requests according to the attacker’s commands, overwhelming the server or network’s capacity. As a result, the system either slows down or becomes completely unusable.
Types of DDoS Attacks
Layer 3 and Layer 4 DDoS Attacks
- ICMP Flood (Ping Flood): Continuous ICMP “Echo Request” packets are sent to the target server. The server tries to respond with “Echo Reply,” exhausting its processing capacity. This attack can lead to system slowdown or crash.
- UDP Flood: Fake UDP packets are sent to different ports on the server. As the server tries to check which port is listening, its resources are depleted. Source IP addresses are often spoofed, making detection harder.
- SYN Flood: Fake SYN packets are sent in the TCP connection process, but the attacker does not complete the three-way handshake. The server keeps ports open while waiting for a SYN-ACK response, consuming resources. This attack can prevent the server from responding to other requests, leading to service disruption.
- NTP Amplification: Fake IP addresses are used to send numerous requests to NTP servers. NTP servers return large responses to the target, overwhelming the network’s capacity.
- DNS Amplification: Large queries, like “ANY,” are sent to DNS servers, exhausting their capacity. DNS servers respond with large responses to the target’s IP address, amplifying the attack’s effect.
Layer 7 (Application Layer) DDoS Attacks
Layer 7 attacks target specific applications to exhaust the processing capacity of servers, often aimed at web, email, or DNS servers.
- HTTP Flood: A large number of HTTP GET or POST requests are sent to the target server. Unable to handle the incoming requests, the server goes offline. These attacks cause major performance issues, especially in web servers.
- Slowloris: A slow but continuous attack that keeps the server’s connections open for as long as possible by sending slow requests. Since all connection slots are full, new requests cannot be processed.
- DNS Flood: Fake queries are sent in large volumes to DNS servers, exceeding their resolution capacity. Users cannot access DNS servers, leading to service interruptions.
- Zero-Day DDoS Attacks: These attacks target unknown or previously undetected vulnerabilities. They can be challenging to counter because existing security measures may not detect these threats.
Why DDoS Attacks Are Dangerous
- Easy Implementation: DDoS attacks require no special technical knowledge. Botnets are easy for attackers to use.
- Defense Difficulty: The multiple sources make detection and blocking difficult.
- Costly Damages: Service interruptions cause financial losses, customer dissatisfaction, and damage to brand reputation.
- IoT Risks: Vulnerable IoT devices can become part of botnets and be used in attacks.
Methods for Detecting DDoS Attacks
- Traffic Analysis: Sudden spikes and unusual patterns in network traffic should be monitored.
- IDS/IPS Usage: Intrusion detection and prevention systems can detect attacks early.
- Source Monitoring: Fake requests can be identified through IP addresses and ports.
- Behavior Analysis: Abnormal user behaviors or unusual request density can be monitored.
Methods for Preventing DDoS Attacks
- Firewalls and IPS/IDS: Provides an effective defense for filtering malicious traffic.
- CDN Usage: Content distribution networks distribute traffic across different servers, balancing the load.
- Network Redundancy: Multiple data centers and backup networks ensure service continuity during attacks.
- Cloud Services: Cloud-based security solutions, with their high bandwidth and distributed structures, resist volume-based attacks.
- Traffic Monitoring and SIEM Systems: Data collection from every corner of the network allows early detection of threats.
Largest DDoS Attacks of 2024: New Threats and Precautions in Cybersecurity
In 2024, Distributed Denial of Service (DDoS) attacks posed serious threats with rapidly evolving new techniques and massive attack volumes, challenging both businesses and cybersecurity professionals. These attacks aimed to disrupt services by overwhelming certain networks or systems with heavy data flows. Affecting sectors from telecommunications to finance, these attacks had a global impact.
January 2024 – Multi-Botnet Attacks (Asia and Europe)
Numerous botnet attacks targeted the telecom and finance sectors in Asia and Europe, generating 1.5 Tbps traffic primarily aimed at L3/L4 layers. These botnets overwhelmed the network’s bandwidth, causing service interruptions.
February 19, 2024 – Mirai Botnet-Based Attack (Hosting Providers in Asia)
A modified version of the Mirai botnet targeted major hosting providers in Asia, generating a 2 Tbps HTTP-based attack at the L7 layer. This attack highlighted infrastructure deficiencies and led to strengthened security layers.
April 3, 2024 – HTTP/2 Rapid Reset Attack (Global)
This global attack exploited a protocol vulnerability in HTTP/2 to terminate server connections quickly. While the attack size was not disclosed, it was observed globally and underscored the need for stronger security layers in the HTTP/2 protocol.
May 2024 – HTTP/2 Continuation Flood Attack (Multiple Regions)
Attackers targeted servers in various regions using HTTP/2 frames to increase memory consumption and overload server capacity, primarily affecting systems with weak memory management at the L7 layer.
July 15, 2024 – Multi-Vector DDoS Attack (Financial Services, Israel)
The financial services sector in Israel was hit with DNS reflection and UDP flood attacks at L3/L4 layers. This multi-vector attack, involving 798 Gbps and 419 TB of data, combined DNS reflection and UDP protocols to stress systems and breach defense protocols.
August 2024 – HTTP Request Flood Attack (Google Cloud)
This attack generated 398 million requests per second (RPS) targeting Google Cloud infrastructure. Known as an HTTP request flood attack, it aimed to slow down Google’s services, revealing the need for greater DDoS flexibility in service providers.
September 2024 – Volumetric DDoS Attack (Cloudflare)
Cloudflare, a global content distribution network provider, countered a 3.8 Tbps volumetric DDoS attack aimed at exhausting its network capacity, once again proving the importance of advanced DDoS prevention technologies.
October 2024 – Ransomware DDoS (RDoS) Attack (Europe and USA)
Companies in Europe and the USA faced ransom-demand DDoS attacks at L3/L4 layers, aiming to create service disruptions and extort ransom. These RDoS attacks show the increasing prevalence of ransom-based DDoS and necessitate tighter security policies.