Cloud Computing Security
Introduction
Cloud computing refers to the storage and processing of data and applications on remote servers accessible over the internet. Cloud computing provides many advantages to organizations, such as cost savings, flexibility, scalability, and efficiency. However, cloud computing also comes with certain challenges and risks from a security perspective. In this article, we will provide information about cloud computing security, particularly focusing on cloud architecture, data security, authentication and authorization, cloud security tools, and best practices.
Cloud Architecture
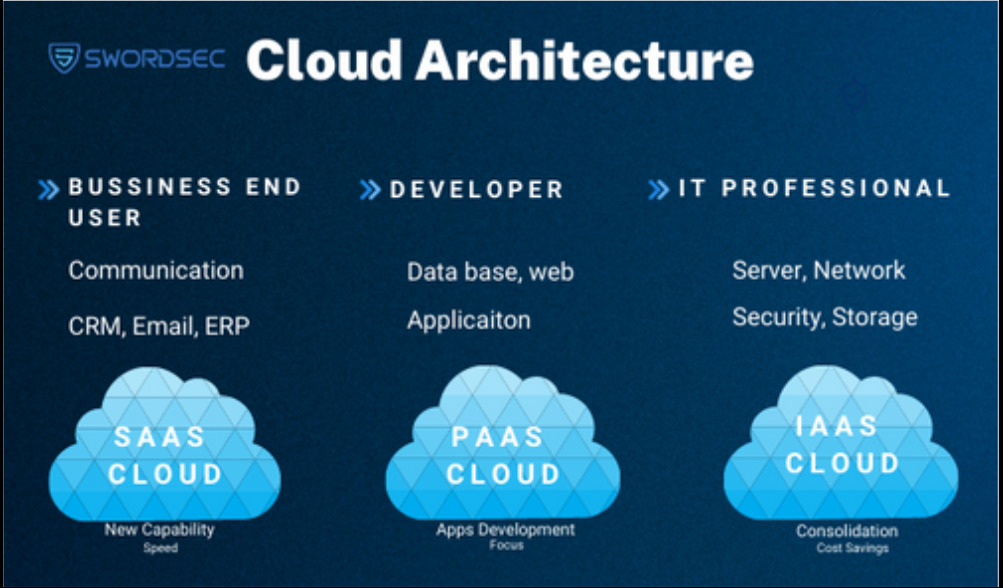
Cloud architecture is a framework that defines how cloud services are designed, deployed, managed, and monitored. Cloud architecture directly impacts the performance, security, availability, and reliability of cloud services. It consists of three main components:
Cloud Service Provider (CSP): The organization that offers and manages cloud services.
Cloud Service Consumer (CSC): The organization that uses cloud services.
Cloud Service Broker (CSB): The entity that acts as an intermediary between the CSP and CSC.
Cloud architecture is also categorized into three fundamental service models:
Infrastructure as a Service (IaaS): Provides CSC with infrastructure resources such as servers, storage, networking, and virtualization.
Platform as a Service (PaaS): Offers CSC platform resources for application development, testing, and deployment.
Software as a Service (SaaS): Allows CSC to use ready-to-use applications.
For ensuring the security of cloud architecture, the CSP must provide security controls, and the CSC must also fulfill its own responsibilities. For instance, in the IaaS model, the CSP is responsible for securing the infrastructure layer, while the CSC is responsible for the security of the operating system, applications, and data layers. In the PaaS model, the CSP secures the platform layer, while the CSC is responsible for the security of the application and data layers. In the SaaS model, the CSP secures the application layer, and the CSC is only responsible for the security of the data layer.
Data Security
Data security refers to the protection of data from unauthorized access, alteration, loss, or damage. In cloud computing, there are four key elements of data security:
Encryption is the process of transforming data into an unintelligible form. Encryption ensures the protection of data during both transmission and storage. There are two main methods of encryption: symmetric encryption and asymmetric encryption. Symmetric encryption uses the same key for encrypting and decrypting data, while asymmetric encryption uses different keys for these operations.
Backup involves creating copies of data in another location to ensure recovery in case of data loss or corruption. Backup ensures data security and continuity. There are two main backup methods: full backup and incremental backup. Full backup involves copying all data, while incremental backup copies only the changed or newly added data.
Recovery is the process of restoring data from backups in the event of data loss or corruption. Recovery ensures data accessibility and integrity. There are two main recovery methods: in-place recovery and off-site recovery. In-place recovery restores data on the same server where it was lost or corrupted, while off-site recovery restores data on a different server.
Deletion involves permanently erasing data. Deletion ensures data confidentiality and compliance. There are two main deletion methods: physical deletion and logical deletion. Physical deletion involves physically destroying or eliminating the storage media where the data is stored. Logical deletion makes data unreadable by overwriting or encrypting it.
By implementing these data security measures, cloud computing services can ensure the protection of sensitive information and maintain the trust of users and customers.
Authentication and Authorization
Authentication and authorization are the two fundamental elements of access control in cloud computing.
Authentication is the process of verifying users’ identities. There are two primary methods of authentication:
Single-factor authentication: Users verify their identity by providing only one piece of information (e.g., password).
Multi-factor authentication: Users verify their identity by providing multiple pieces of information (e.g., password, PIN code, biometric feature) or using a device they possess (e.g., a smartphone).
Authorization, on the other hand, is the process of determining which resources users can access. There are two main methods of authorization:
Role-Based Access Control (RBAC): It determines users’ access based on their roles. For example, a system administrator may have access to all resources, while an employee may only have access to the resources assigned to them.
Attribute-Based Access Control (ABAC): It determines users’ access based on the attributes of users, resources, and the environment. For example, an employee may have access to resources only during specific hours, from a certain location, and using a specific device.
ABAC is more flexible and dynamic compared to RBAC
Cloud Security Tools
Cloud security tools are software or hardware solutions used to prevent, detect, and manage security risks in cloud computing. These tools offer various functions to enhance the security of cloud services. For example:
Cloud Security Firewall: Monitors cloud traffic and blocks malicious or unwanted network packets.
Cloud Security Gateway: Ensures the encryption, prevention of data leaks, and compliance of cloud data.
Cloud Security Analytics: Analyzes events and behaviors in the cloud environment to report abnormal or suspicious activities.
Cloud Security Audit: Evaluates the security status of cloud services to identify weaknesses or deficiencies.
The selection and use of cloud security tools depend on the cloud service model, cloud deployment model, cloud service provider, and the organization’s needs. For instance, in the IaaS model, the cloud service consumer may require more security tools since they have more control. In contrast, in the PaaS or SaaS model, the cloud service provider may need fewer security tools since they have more control. Additionally, in a private cloud, the organization can choose its security tools, whereas in a public cloud, they might have to use the security tools provided by the CSP.
Using cloud security tools is a critical step in ensuring security in cloud computing. However, it is not sufficient on its own. Organizations must also follow best practices for cloud computing security.
Best Practices for Cloud Computing Security
Best practices for cloud computing security are rules or methods that organizations should follow to prevent or reduce security issues they may encounter in cloud computing. Some of the best practices for cloud computing security include:
Carefully selecting a cloud service provider: Organizations should review the security controls, certifications, contracts, and policies offered by cloud service providers and choose the one that aligns with their needs.
Sharing responsibility based on the cloud service model: Organizations should be aware of their responsibilities for security in different layers based on the cloud service model and take appropriate security measures for those layers.
Encrypting, backing up, and deleting data: Organizations should ensure that data is encrypted during transmission and storage, regularly backed up, and appropriately deleted or destroyed when needed.
Implementing authentication and authorization systems: Organizations should establish effective authentication and authorization systems to verify users’ identities and determine their access to resources.
Using cloud security tools: Organizations should employ suitable cloud security tools to prevent, detect, and manage security risks in the cloud environment.
Providing cloud security training: Organizations should regularly provide cloud security training to their employees to ensure they are aware and competent in cloud computing security practices.
Conclusion
Cloud computing is a technology that provides many benefits to organizations. However, it also presents some challenges and risks from a security perspective. Therefore, organizations need to be cautious and well-informed about cloud computing security. In this blog post, we provided information about cloud computing security, particularly focusing on cloud architecture, data security, authentication and authorization, cloud security tools, and best practices. We hope this article has been helpful to you

