Reverse Shell and Backdoor: What Are the Differences?
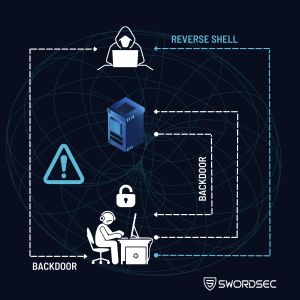
Understanding the concepts of Backdoor and Reverse Shell enables you to acquire knowledge about computer and network security. By grasping the differences between these two mechanisms, you can better protect your computer and systems against potential attacks. Furthermore, this information will make you more aware of computer security, helping you recognize potential threats. Remember, knowledge is power, and utilizing this power for your security is crucial.
What is Backdoor?
Backdoors are methods that bypass computer security measures unnoticed. For example, a Trojan backdoor can enable unauthorized users to access a computer, network, or software. Unlike other viruses, backdoors infiltrate the operating system disguised as drivers or other low-level programs. According to the hierarchical ring system, backdoors reside in Ring 2 and have the same priority as the operating system kernel. Anything operating in Ring 2 can control all processes in Ring 3 and 4. From this, we observe that such deep integration allows the attacker to gain complete access to the entire system
How Backdoors Work?
When computers are infected with a backdoor, they often become ‘zombies’ in a botnet. Machines controlled by the botnet continue to operate normally until they receive a command from the control server. Once a backdoor is opened, lightweight versions of backdoors emerge to help expand the botnet. Machines that masquerade as their true owners launch DDoS attacks and spam to ensure anonymity. If this happens to you, you might get banned from sites you never visited. However, this is just one way backdoors operate. More commonly, an infected PC sends spam with attached files or links.”
Reverse Shell, Why is it Important in terms of Cybersecurity?
The concept of a Reverse Shell is one of the critical aspects of cybersecurity. The ability of attackers to exploit vulnerable systems and gain complete control over operating systems poses a significant cybersecurity threat.
What is Reverse Shell and How Does it Work?
Reverse Shell is a method that allows attackers to connect to remote computers through firewalls. It is used when conventional methods are not successful. Reverse Shell enables cybercriminals to execute arbitrary commands on operating systems and gain full control over the target computers.
The underlying logic behind the use of Reverse Shell is to connect to a controlled computer and request a shell session during a typical remote shell setup. If direct access to the remote host is not possible, Reverse Shell comes into play. It connects to a listening network host from the outside and creates a shell session, providing attackers access to the target computer’s operating system.
Reverse Shell can be used specifically to provide remote management for computers behind Network Address Translation (NAT); therefore, it is also important for legitimate administrative purposes. However, cybercriminals can exploit these features by executing operating system commands on protected computers behind firewalls or other network security systems. For example, malware installed on local stations through phishing emails or malicious websites can initiate external connections to command servers and provide attackers with Reverse Shell capabilities. However, due to traffic filtering by firewalls, connections to listening servers will often be successful.
As a result, the concept of Reverse Shell holds great significance in terms of cybersecurity. It can be used for both legitimate administrative purposes and enable malicious activities by cybercriminals. Computer users and network administrators should consider this method carefully. Therefore, it is essential to increase security measures and be conscious to avoid being vulnerable to such threats posed by cybercriminals.
Backdoor and Reverse Shell: Their Differences in Terms of Cybersecurit
In the world of cybersecurity, we often encounter terms like ‘Backdoor’ and ‘Reverse Shell.’ These two concepts are methods used by attackers to gain control over systems and networks. So, what are the fundamental differences between backdoors and reverse shells?
A Backdoor is a broader concept and can be thought of as any mechanism that provides unauthorized access to a system. On the other hand, a Reverse Shell is a specific technique used to execute commands remotely on a system. Backdoors are commonly used as part of malicious software, while Reverse Shells are one of the methods attackers resort to for gaining more control over target systems.
In conclusion, Backdoor and Reverse Shell concepts hold significant importance in cybersecurity. Understanding the differences between these terms can help establish a more effective defense against cyber threats. Therefore, it is essential to raise cybersecurity awareness and be prepared against such threats.